A new malspam campaign is abusing icon files to dupe victims into executing the NanoCore Trojan.
On Thursday, SpiderLabs at Trustwave said a recent phishing campaign has outlined a technique for spreading NanoCore, a remote access Trojan (RAT).
The emails pretend to be from a “Purchase Manager” of organizations that are being spoofed, such as legitimate business partners. These phishing messages contain an attachment, named “NEW PURCHASE ORDER.pdf*.zipx,” which are actually image binary files.
The icons have additional information attached to them in a .RAR format.
By using an icon file, the fraudsters are likely attempting to avoid security and protections offered by email gateways.
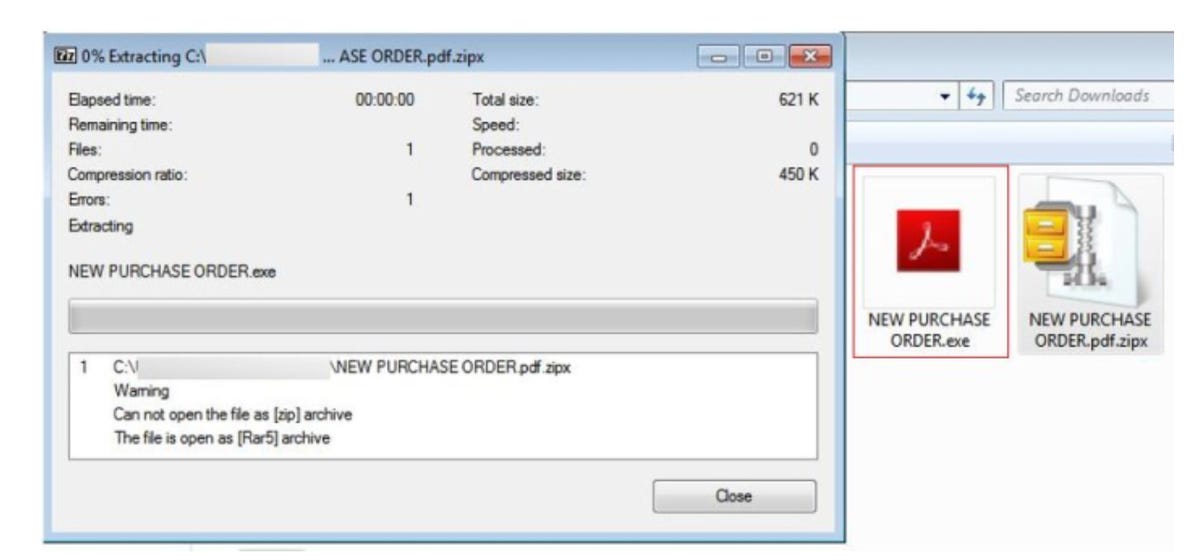
If the victim clicks on the attachment and their PC has an unzip tool installed, such as WinZip or WinRAR, an executable file is extracted. 7Zip, too, can extract the file — but it takes more than one attempt.
“There is no need for the extension of the recent attachments to be renamed to something else other than .zipx or .zip just for their executables to be extracted using 7Zip,” the researchers say.
Successful extraction leads to the deployment of NanoCore RAT version 1.2.2.0. First detected in the wild in 2013, this Remote Access Trojan (RAT) includes a keylogger, information stealer, dropper for additional malware, and also contains the ability to access and steal webcam footage as well as exfiltrate data to send to a command-and-control (C2) server.
The malware has been sold previously in underground forums and is often spread through financially-related phishing campaigns.
This version of the Trojan is able to create copies of itself within the AppData folder and will also compromise the RegSvcs.exe process. Information stolen by the malware is sent to multiple C2s.
The technique noted by SpiderLabs is similar to a past phishing campaign that also utilized .zipx. In 2019, the researchers said in a blog post that Lokibot, another Trojan that also includes the ability to compromise cryptocurrency wallets, was being spread in malspam campaigns through a .zipx extension and .JPG icons.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0





































