Research into how rootkits are used by cybercriminals has revealed that close to half of campaigns are focused on compromising government systems.
On Wednesday, Positive Technologies released a report on the evolution and application of rootkits in cyberattacks, noting that 77% of rootkits are utilized for cyberespionage.
Rootkits are used to obtain privileges in an infected system, either at the kernel level or based on user modes, the latter of which is used by many software applications. Some rootkits may also combine both capabilities.
Once a rootkit has hooked into a machine, it may be used to hijack a PC, intercept system calls, replace software and processes, and they may also be part of a wider exploit kit containing other modules such as keyloggers, data theft malware, and cryptocurrency miners — with the rootkit set to disguise malicious activity.
However, rootkits are difficult to develop and may take both time and expense to do so — and as a result, the majority of rootkit-based attacks are linked to advanced persistent threat (APT) groups that have the resources and skill to develop this form of malware.
The researchers’ analysis sample was made up of 16 malware types; 38% being kernel-mode rootkits, 31% user-mode, and 31% combination-type rootkits. The majority of which in use today are designed to attack Windows systems.
According to Positive Technologies, there appears to be a general trend to user-mode rootkits in the exploit industry due to the difficulty of creating kernel-mode variants, and despite improvements in defense against rootkits in modern machines, they are often still successful in cyberattacks.
“It takes a lot of time to develop or modify such a rootkit, and this can make working to time constraints difficult; you must be quick to exploit a vulnerability in a company’s perimeter before it is noticed and security updates are installed, or another group takes advantage of it,” Positive Technologies says. “Because of this attackers are used to acting quickly: it can take less than a day from the moment the exploit is identified to the first attempts to make use of it, and if a group does not have a reliable, ready-to-use tool, this time is clearly not enough to work on it.”
In addition, the team says that any errors in the coding of a kernel-mode rootkit can lead to a machine’s destruction and permanent corruption, and so if a financial demand is being made — for example, by ransomware operators — then the harm caused would stop extortion attempts from being successful.
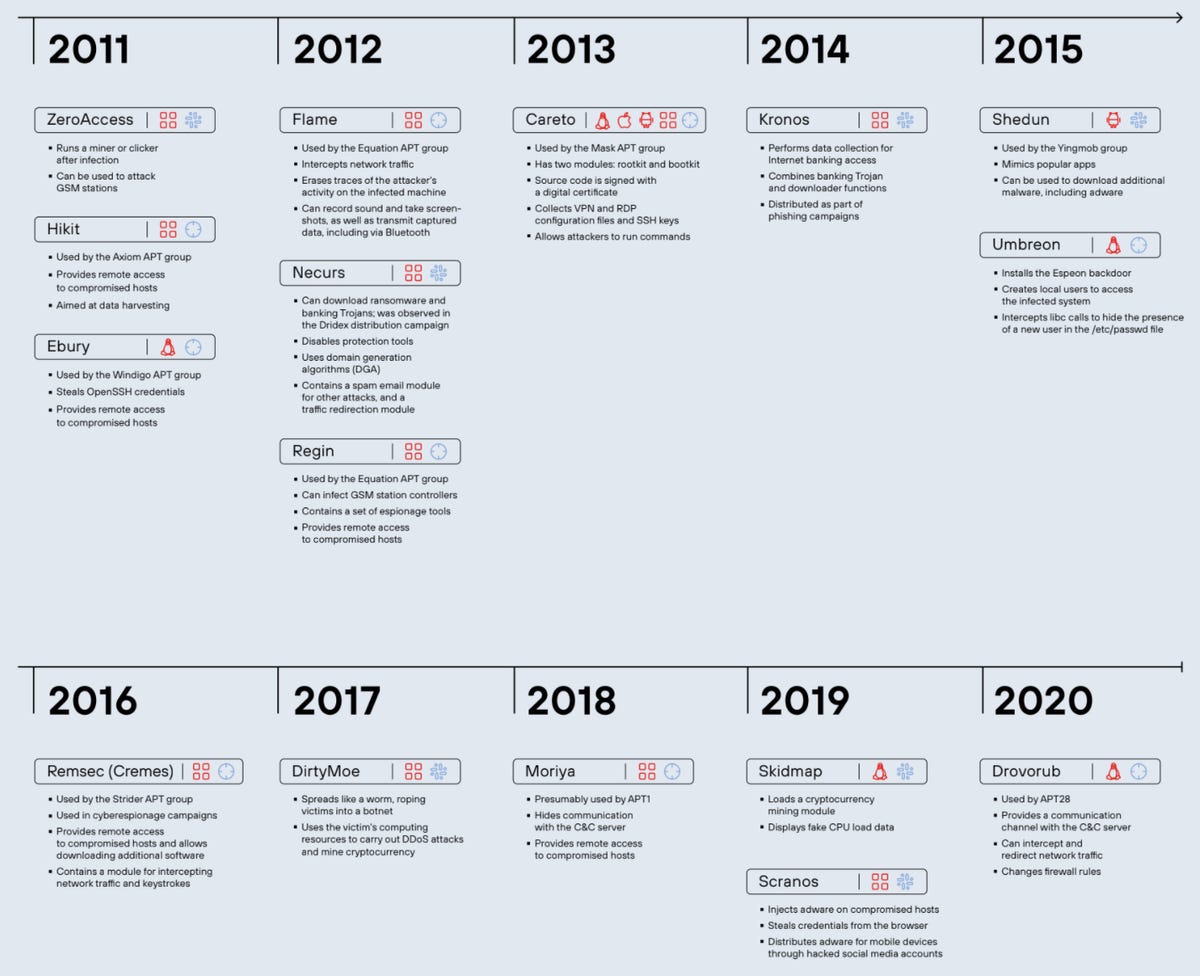
In 44% of cases documented since 2011, rootkits have been used to strike government agencies worldwide, followed by research and academic institutions in 38% of known campaigns.
Positive Technologies suggests that when rootkits are in play, their cost and development time require a high-value target: and in the majority of cases, the aim is data theft — although the goal is sometimes purely financial.
In addition, rootkits are most often tracked to attacks against telecommunications companies, the manufacturing sector, and banks or financial services.
Rootkits may also be employed in targeted attacks against individuals, said to be “high-ranking officials, diplomats, and employees of victim organizations,” according to the researchers.
Commercially available rootkits often fetch a price of between $45,000 and $100,000, depending on the target operating system, terms of subscription, and features.
“Despite the difficulties of developing such programs, every year we see the emergence of new versions of rootkits with a different operating mechanism to that of known malware,” commented Alexey Vishnyakov, Head of Malware Detection at the Positive Technologies Expert Security Center (PT ESC). “This indicates that cybercriminals are still developing tools to disguise malicious activity and coming up with new techniques for bypassing security — a new version of Windows appears, and malware developers immediately create rootkits for it. We expect rootkits to carry on being used by well-organized APT groups.”
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0






















