- Across the USA, Europe and Asia, there was an increase in the number of attacks targeting the education and research sector in recent months.
- The USA witnessed an increase in DDOS attacks, while there was an increase in information disclosure attempts in Europe. Asia meanwhile, faced an increase in vulnerability exploits.
July and August signals the start of the academic year for millions of students. However, because of the pandemic, back-to-school is different this year, with many students attending classes remotely from their homes. As previously reported, researchers at Check Point found that in the last 3 months, there was a surge in hacker interest in topics related to education, research and going back to school. Now that the new academic year has begun, we wanted to look deeper into the characteristics of these attacks.
Specifically, we looked into the USA, Europe and Asia. Overall, education & research in these geographies is proving to be an attractive sector for cybercriminals to target. Our data shows an increase in attacks, with different methods and tactics being adopted in different regions.
The USA presents the highest increase in academic and research related attacks
The average number of weekly attacks per organization in the academic sector in July-August increased by 30% from 468 to 608 when compared to the previous two months. The general increase when you consider all sectors in the USA is only 6.5%.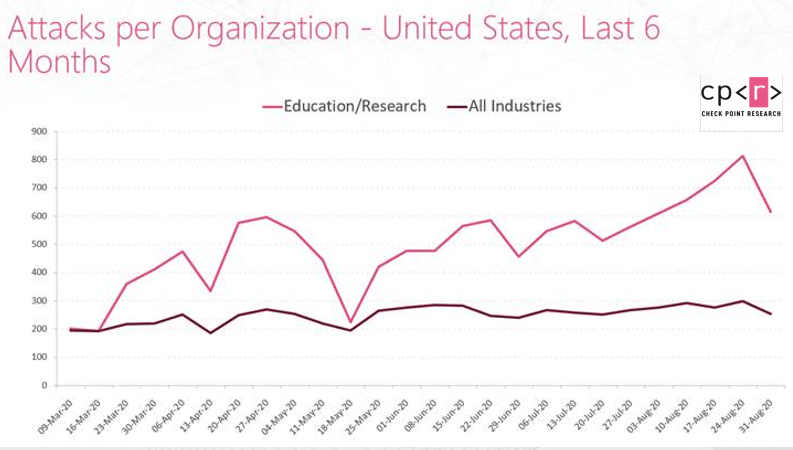
We found that the main increase came from DDos attacks (a category of malicious cyber-attacks employed to make an online service, network resource or host machine unavailable to its intended users on the Internet). A a recent example involved a teen hacker in Florida who paralyzed the nation’s largest school districts for its first three days of virtual classes. He was subsequently charged.
DoS/DDoS attacks are on the rise and a major cause of network downtime. Whether executed by hacktivists to draw attention to a cause, fraudsters trying to illegally obtain data or funds, or a result of geopolitical events, DDoS attacks are a destructive cyber weapon. Beyond education and research, organizations from across all sectors face such attacks daily.
Check Point’s Zero Day DDoS Protection Blocks a wide range of attacks with customized multi-layered protection. DDoS Protector Security Appliances and Cloud DDoS Protection Services block destructive DDoS attacks before they cause damage.
Europe education and research institutions face an increase in information disclosure attempts
In Europe, there was an increase in the number of attacks, noticeably in information disclosure attempts. The average number of weekly attacks per organization in the academic sector in July-August increased by 24% from 638 to 793 in the previous two months. The general increase in the number of attacks when you consider all sectors in Europe, in contrast, is only 9%.
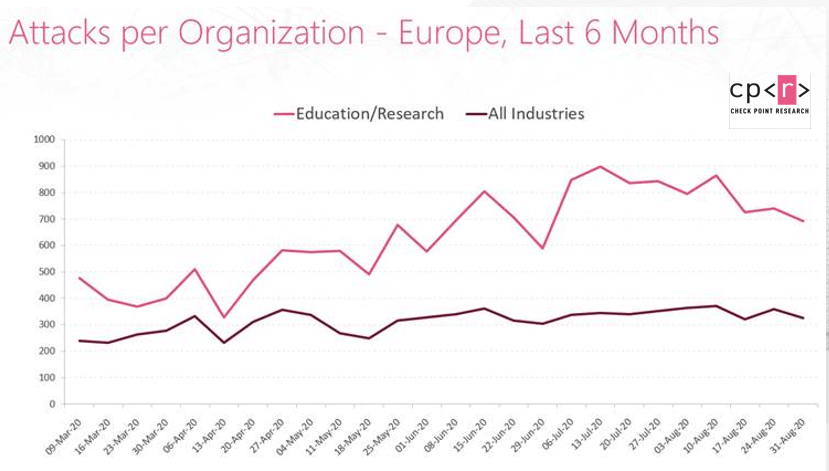
Recently, Newcastle University in the United Kingdom suffered from a ransomware cyberattack that disrupted its network and IT systems. Its medical sciences faculty had to register 1,000 returning students manually as a result. University officials have said it would take weeks to recover.
Vulnerability exploits in Asia
In Asia, the increase in attacks was seen mainly in several types of vulnerability exploits: Denial of Service, Remote Code Execution and Information Disclosure. The average weekly attacks per organization in the academic sector in July-August increased by 21% from 1322 to 1598 when compared to the previous two months. The general increase in the number of attacks when you consider all sectors in Asia is only 3.5%.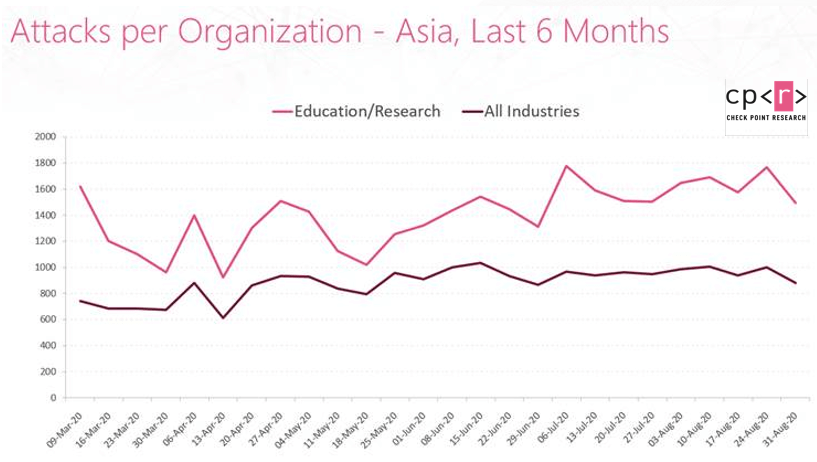
Best practices to elevate endpoint security
- Reduce attack surface: A common approach in information security is to reduce the attack surface. For endpoints, you need to take full control of peripherals, applications, network traffic, and your data. You need to encrypt data in motion, at rest, and when it’s in use. It is also important to make sure you enforce your corporate policies to achieve endpoint security compliance
- Prevent before it runs: first block known attacks by using endpoint anti-malware and reputation, and then prevent unknown attacks. To thwart various exploits, use anti-exploit technology to prevent drive-by attacks and protect your applications. Finally, you can inhibit user mistakes by implementing zero-phishing technology that blocks phishing sites, prevents credential re-use, and detects compromised passwords.
- Runtime Protection: Anti-ransomware technology allows you to detect signs of ransomware and uncover running mutations of known and unknown malware families by using behavioral analysis and generic rules
- Contain and remediate: Contain attacks and control damages by detecting and blocking command and control traffic and prevent the lateral movement of malware by isolating infected machines. You can then remediate and sterilize your environment by restoring encrypted files, quarantining files, kill processes, and sterilizing the full attack chain.
- Understand and respond: The final principle is to know you must quickly triage events, understand the full nature of the attack, and immunize other surfaces by sharing Indicator of Compromise (IoC) and Indicator of Attack (IoA) information.

























