While IoT security standards lag, IoT security companies innovate – Overview of trends in IoT cybersecurity
By Gil Yankovitch, Firmware Technology Lead and Ram Yonish, Firmware Security Evangelist (former co-founders of Cymplify Security, acquired by Check Point)
While IoT and OT devices proliferate, IoT security standards and regulations are few and far between. Unsurprisingly, this puts individuals, enterprises and states at major risk. In this post, we present some of the leading IoT cybersecurity solutions that have emerged in the last few years, as well as some of the drivers motivating device manufacturers to build better-secured devices.
From IP cameras and elevators to medical devices and industrial controllers, IoT devices are inherently vulnerable and easy to hack. Many of these devices run on unpatched software, are misconfigured, or use unsecured communication protocols. Furthermore, organizations own extensive and diverse device inventories of multiple vendors, models and functionalities, with many shadow unmanaged devices connected to the network without anyone’s knowledge. And while IoT environments have become increasingly complex, IT security solutions have remained far behind, with limited visibility and control over IoT devices and their associated risks. This security gap increases the risk of a successful cyber-attack where critical devices can be shut down, damaged, manipulated, or used to infect other systems on the network.
Kaspersky H1 2019 report for IoT attacks:
Kaspersky detected 105 million attacks on IoT devices coming from 276,000 unique IP addresses in the first six months of 2019. This figure is around nine times more than the number found in H1 2018. The majority of the attacks stemmed from the Mirai (39%) and Nyadrop (also 39%) malware families.
Network-based IoT Security
IoT network-based solutions are mostly suitable for organizations looking to protect the many different types of IoT devices connected to their network. According to a research study by Dimensional Data, “90% report their companies have some shadow IOT devices, 44% mentioning at least half are connect without CISO knowledge.”
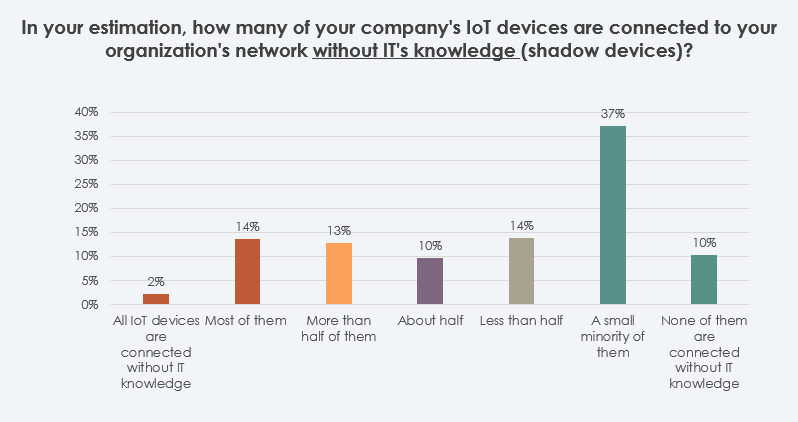
Figure 1: Source: Why Security Consolidation Matters, by Dimensional Data
Most of the solutions in this area offer an agentless method of auto-discovering managed and unmanaged connected IoT devices and OT assets, tagging them based on their attributes (e.g., device type, manufacturer, model, firmware version, and MAC address), analyzing their behavior in real-time to detect anomalies and also offer mitigation steps.
These activities can be done manually or automatically, to isolate a compromised device or stop the attack by enforcing IoT-related security rules within an organization’s security controls, including NAC, security gateways and network switches.
These solutions mainly focus on identifying the asset on the protected network, analyzing the ongoing traffic stream passively (e.g. by port-mirroring the organization’s network) and learning what constitutes normal network activity and protocols in order to detect anomalies.
Security vendors in this space focus on different industry verticals, learning and modeling their threat analysis and anomaly engines according to each industry’s standard protocols. That way, each vendor brings industry-specific domain-expertise and applies their knowledge to best define what a secure network should look like, across every device in every field.
The main advantage of using these solutions is that they are relatively easy to deploy, are cloud-based, with minimal impact on protected assets and devices, or the organizational network.
Leading IoT discovery vendors in this list include companies like Armis, Ordr, Claroty, Tenable.OT (formerly Indegy), Medigate, CyberMDX and ScadaFence. Check Point also offers a network-based IoT security solution by providing its management and enforcement capabilities seamlessly integrated with the above IoT discovery engines.
On-device protection
On-device IoT security solutions are the latest generation of IoT cyber protection. These solutions require a deep understanding of the device’s behavior, offering protection from new and different attack vectors than network-based solutions. To name some examples:
- Runtime protection: This method involve analyzing the device firmware, mapping the correct behavior of the device’s operating system and software, then monitoring that behavior at runtime. Most of the current solutions as of today are based on the Control Flow Integrity (CFI) mechanism. Companies offering this solution are Check Point (after acquiring Cymplify Security), Karamba Security and Vdoo. Run-time protection solutions focus on the device’s behavior as a computing machine that acts according to certain computing rules. Deviations from expected behavior, such as unauthorized writes to certain parts of the file system or firmware, or rogue processes that shouldn’t spawn are identified. Runtime protection goes even deeper to identify attempts to hook the control flow of each one of the protected processes in memory, on the device itself, constantly instrumenting their execution and making sure their flow is not diverted by any type of attack.
- Secure boot solutions: Secure boot is a process whereby your OS boot images and code are authenticated against the hardware root of trust right those boot images are allowed to be executed during the boot process. The hardware must be set up beforehand in such a way that it only executes code that was cryptographically signed with the manufacturer’s, or any other trusted, credentials. Companies offering this protection method are: ARM (Using their TrustZone technology), Samsung (Using Knox on top of TrustZone), and Synopsys. Another approach is Nanolock’s device-level, Security by Design solution protecting IoT and connected edge devices against cyberattacks, leveraging the device’s flash memory to create a root of trust, and extend a powerful flash-to-cloud defense that secures the entire chain of device vulnerability– from deeply embedded endpoints in the device, to the cloud — with minimal computing power. The technology is considered an alternative to Secure Boot and can protect low-resource (CPU & energy) devices.
- On-chip protection: This approach is taken by the larger software companies and hardware manufacturers, offering device-level security as part of a broader ecosystem. These companies (including Microsoft, ARM) offer secure hardware platforms alongside their software security suites, so vendors develop their products on-top of their secure platform, benefitting from a broad technology ecosystem. On-chip protection mechanisms usually support things like TPM (Trusted Programmable Module) to store encryption keys, Enclaves (Such as Intel’s SGX), ARM’s TEE (Trusted Execution Environment). All these are then bundled up together to a hardware platform, and are offered as an SDK by the vendor. Secure products are then developed on top of these boards.
Why should device manufacturers invest more in building IoT security into their devices?
While there are no standards and regulations yet, it is clear that more secured devices are of essence to us all; consumers as well as enterprises and nations. New cybersecurity regulations for IoT will come into effect in the next 1-3 years but more importantly, the need for secure devices is a growing need posed by the customers themselves.
One study showed that customers are worried by IoT security and would be willing to pay 22% more, and buy 70% more of secured IoT devices.
Why 5G architecture is a major catalyst for more secure devices
As we enter the 5G generation, IoT devices will be able to interact with different devices directly or through small networks, not necessarily routing traffic through a telco’s secure gateway. As 5G networks are rolled out, the need to find a better solution to protect these devices is quickly hitting home. And the most reasonable and affordable method of protection today one is built-in on-device security.
To quote one research study, 5G requires new approaches to cybersecurity, as “The network has moved away from centralized, hardware-based switching to distributed, software-defined digital routing. Previous networks were hub-and-spoke designs in which everything came to hardware choke points where cyber hygiene could be practiced. In the 5G software-defined network, however, that activity is pushed outward to a web of digital routers throughout the network, thus denying the potential for chokepoint inspection and control”
What should customers do to get more security into their devices?
In order to get more security into consumer devices such as smart TVs, printers, smart locks and IP cameras, as well as secure smart city assets like smart transportation, smart traffic-lights and smart meters, in industry 4.0 devices like PLCs, robots and smart machinery, we all have to push manufacturers to build more security into their devices.
As consumers, we can:
- Change our devices’ default passwords
- Update the devices’ firmware or just reboot the device from time to time
- Keep access to IoT devices restricted by a local VPN
- Buy more devices from companies that put more emphasis on security
As enterprises and large-scale deployers, we can:
- Implement network-level IoT security controls, including IoT discovery and risk analysis, zero trust segmentation and multi-layer IoT Threat prevention
- Ask manufacturers to undergo firmware security assessments so they can uncover security flaws in their devices, including those in third party components
- Request that manufacturers add on-device runtime protection to new devices in the future
As IoT and OT manufacturers, we can:
- Harden our firmware by uncovering security gaps in advance and taking the appropriate corrective measures
- Add on-device runtime protection to protect connected assets at the device level, and prevent zero-day attacks even when operating in unsafe networks
As governments, we should:
- Define cybersecurity standards and regulations
- Promote device security labeling, which requires device manufacturer to add their security score based on standards prescribed by regulatory bodies, just like those mandated for rating a car’s safety or pollution levels.

























