Worming their way in: cybercriminal tricks of the trade
These days, many companies distribute marketing newsletters via online platforms. In terms of capabilities, such platforms are quite diverse: they send out advertising and informational messages, harvest statistics (for example, about clicked links in emails), and the like. At the same time, such services attract both spammers, who use them to send their own mailings, and cybercriminals, who try to gain access to user accounts, usually through phishing. As a result, attackers also get their hands on user-created mailing lists, which allows them to disseminate mass advertising or phishing messages that filtering systems sometimes let through.
Accordingly, in Q3 we registered an increase in the number of messages sent using the Sendgrid platform. A significant portion of them were phishing attacks aimed at stealing login credentials for major resources. The emails were no different from traditional phishing, save for the legitimate headers and link to Sendgrid, which redirected the recipient to a phishing site. To the observant eye, the address bar and From field would reveal the messages to be fake.
Call me!
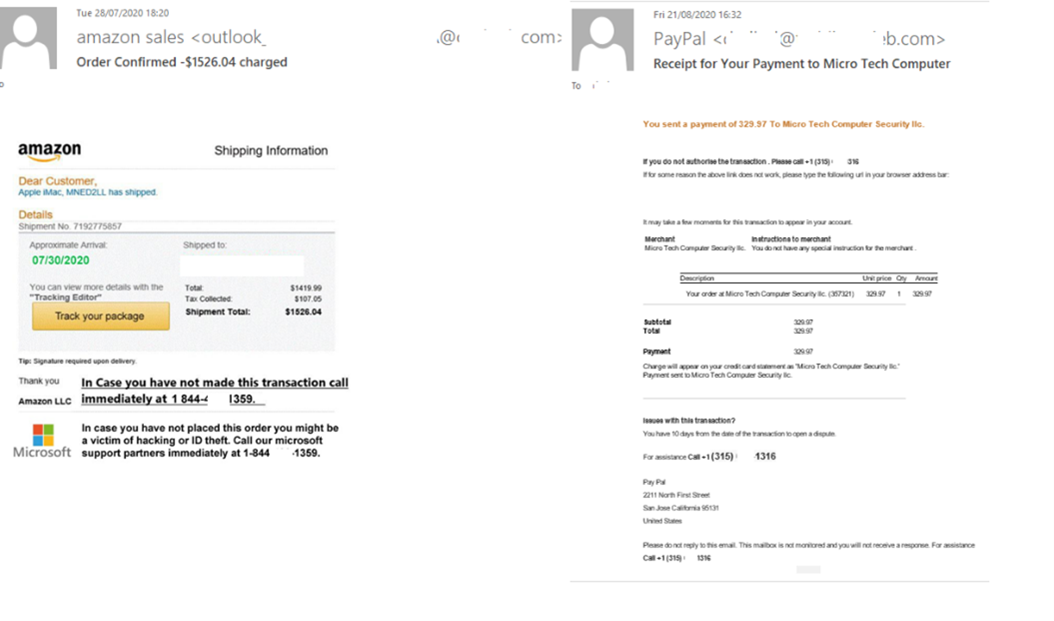
In our previous quarterly report, we talked about an increasingly common scam whereby fraudsters send emails purportedly from large companies with a request to urgently contact support at the given phone number. Users who contacted the operator were then asked for information, such as bank card details, which could then be used to empty their account. The most commonly used toll-free numbers have specific three-digit prefixes after the country code (for example: 800, 888, 844).
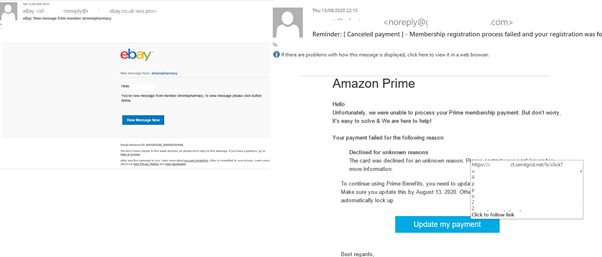
In Q3 2020, we observed new versions of such schemes warning not only about unauthorized account access, but about money transactions supposedly made by the user. The attackers’ calculation is that, on seeing a message about a financial transaction, the client will grab their phone and dial the support number highlighted in bold. Such emails do not contain links, and the message itself is an image, which makes it harder to detect.
Scammers like such schemes, because sending spam is much cheaper and easier than calling potential victims. To avoid swallowing the bait, either call the support service using the number on the organization’s official website (not the one in the email), or use an app that protects against telephone fraud by checking outgoing call numbers.
COVID-19 and spam topics
Facebook grants
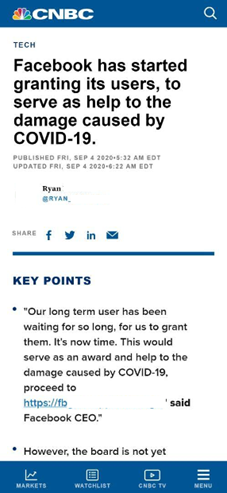
In Q3 2020, many users of social networks and messengers saw a screenshot with some interesting news: CNBC, it said (in broken English — always a red flag), had reported that Facebook was paying out compensation to victims of COVID-19. To get yours, all you had to do was follow the link and fill out a number of documents.
The link had nothing to do with Facebook and led to a fake page resembling the website of Mercy Corps, an organization dedicated to helping victims of natural disasters and armed conflict. To apply, you had to enter your Facebook username and password, then verify your identity by providing personal information, including SSN (social security number, issued to US citizens). This last detail suggests that the attack was aimed at US residents. Users that entered all the requested data gave the cybercriminals not only access to their social network account, but also personal information that could then be used for identity theft or bank card fraud.
It should be noted that the scheme was based on official news that Facebook was indeed ready to provide support to victims of COVID-19. But it only concerned grants for companies, not individuals.
Tourist phishing
The coronavirus pandemic — which has decimated the tourist trade — has also had an effect on scammers: this quarter saw fewer emails offering attractive summer breaks than usual. However, the pandemic did not stop scammers, only redirected their attention.
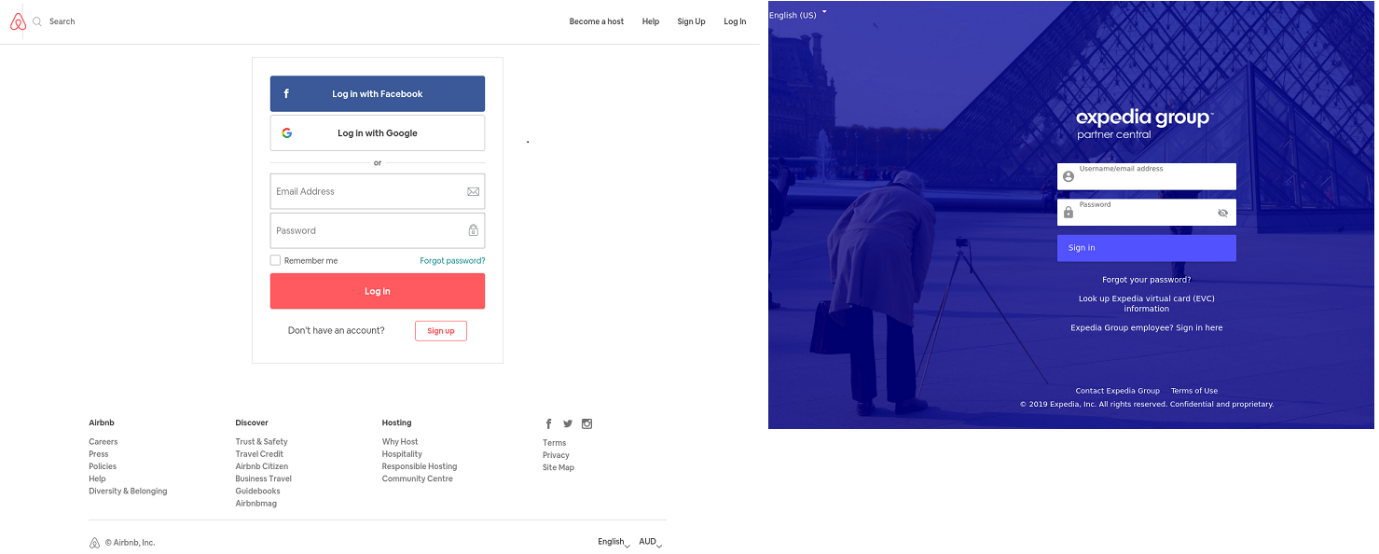
In Q3, Airbnb and Expedia Group users were the most frequent targets of phishing attacks. Fake pages hungry for user credentials were very faithful to the design of the official websites, distinguishable only by looking closely at the address bar, where most often the domain was unrelated to the target company or belonged to a free hosting service.
So as not to reveal their cards too soon, scammers use URL-shortening services and distribute messages in social networks and messengers where shortened links look organic. In their messages, scammers offer cheap tickets or bargain hotel deals. And it is impossible to know where such links lead before clicking them, which is what attackers play upon. Accounts stolen in this way can be used, for example, for money laundering.
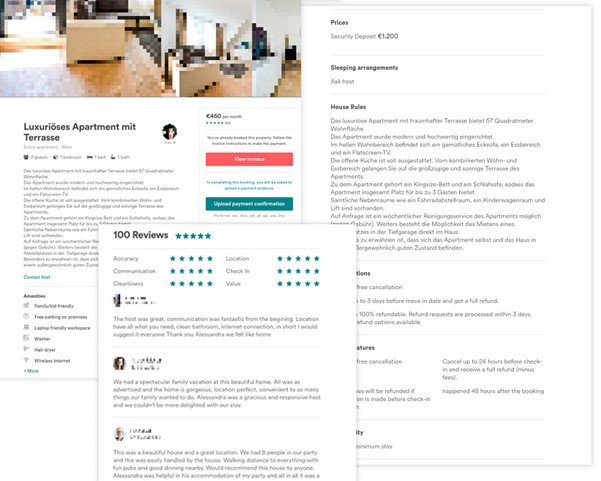
Phishers also forged pages with rental offers: visitors could view photos of apartments and read detailed information about the alleged terms and conditions. Lower down the page were rave reviews from past clients intended to lull the victim into a false sense of security.
The “landlord” in each case agreed to rent out the apartment, but asked for an advance payment. And then disappeared as soon as the money was deposited, together with the fake page. In this instance, the cybercriminals also banked on the fact that the juicy offer (low price, big discount) would distract the victim from looking at the URL and checking the information on the site.
Attacks on the corporate sector
Malicious mail
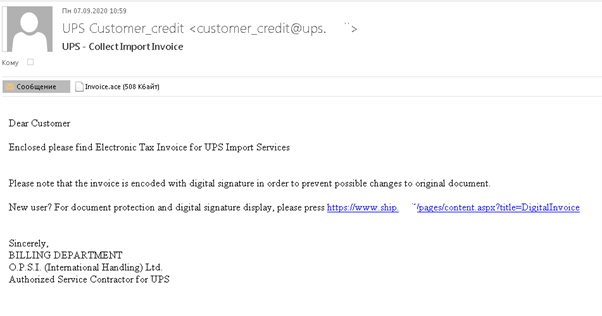
We already told about the distribution of malicious files disguised as notifications from delivery services. They continued this quarter as well: we uncovered a mailing targeting employees connected to sales in some capacity. The scammers persuaded recipients to open the attached documents supposedly to pay customs duties for the import of goods. Instead of documents, the attachment contained Backdoor.MSIL.Crysan.gen.
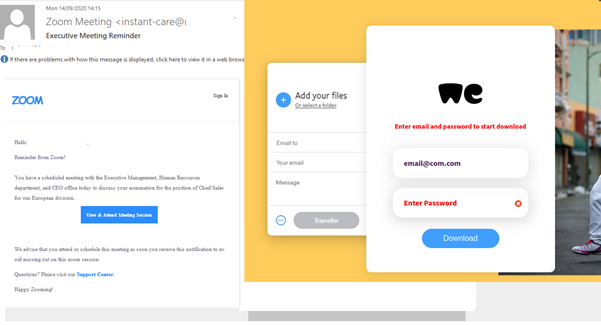
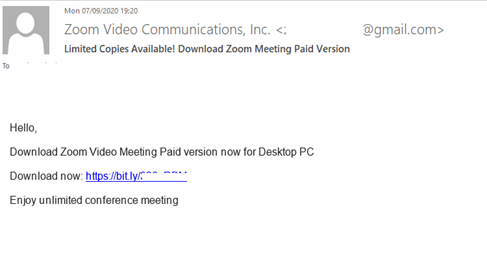
Malicious mailings with “reminders” about online meetups are worth a separate mention. For example, one of them asked the recipient to join a Zoom conference by clicking the attached link. Instead of a meeting, the user ended up on a WeTransfer phishing page. If the user fell for the trap and entered their WeTransfer credentials, the attackers gained access to the company’s files stored in this cloud.
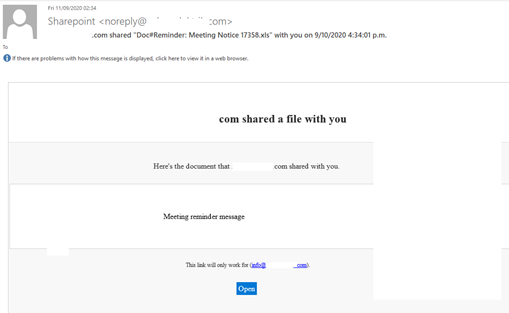
Another mailing informed users that a Microsoft SharePoint document had been shared with them. After clicking the link, the victim was taken to a fake Microsoft login page that helped cybercriminals steal account usernames and passwords.
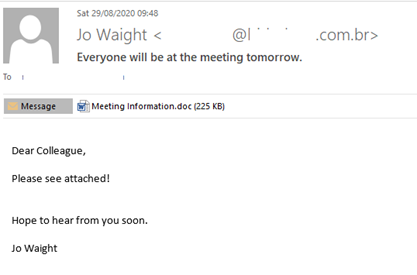
Far more dangerous were meeting notifications containing malicious files. For example, the at-first-glance harmless message below contained HEUR:Trojan-Downloader.Script.Generic.
And Trojan-Banker.Win32.ClipBanker, downloaded via the link in the email below, is used to steal financial (including cryptocurrency-related) information.
Mail scanner
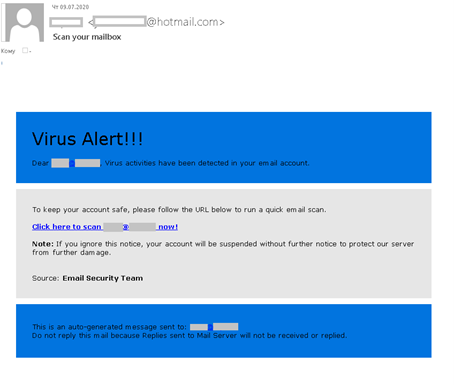
To gain access to corporate accounts, cybercriminals distributed messages stating that a virus had been found in the recipient’s mailbox, and advising an urgent scan, otherwise the account would be disabled. The messages, disguised as notifications from infosec companies, were sent from a free mail address and employed neutral names like Email Security Team to avoid unnecessary specifics.
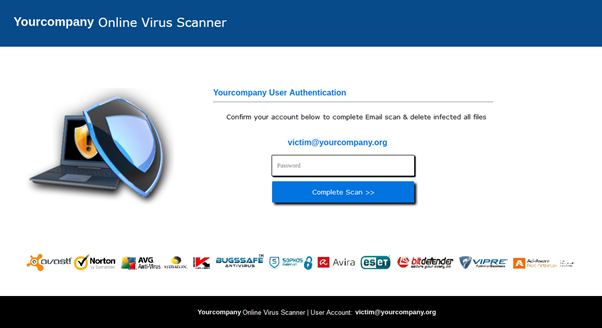
The cybercriminals reckoned on the combined threat of a computer virus and a deactivated work email account forcing the recipient to ignore some of the oddities of the message. For example, such emails could be from the company’s IT or security department, but not a third party. The page that opened on clicking the link did not resemble a corporate resource by either its address or layout. Plus, for added believability, the cybervillains placed on it the logos of all major infosec companies.
To start a “virus scan”, the user was asked to enter the username and password for their corporate mailbox. That said, the “scan” started even if arbitrary credentials were entered in the fields:
Statistics: spam
Proportion of spam in mail traffic
Proportion of spam in global mail traffic, Q2 2020 – Q3 2020 (download)
In Q3 2020, the largest share of spam was recorded in August (50.07%). The average share of spam in global mail traffic was 48.91%, down 1.27 p.p. against the previous reporting period.
Sources of spam by country
Sources of spam by country, Q3 2020 (download)
The Top 5 countries by amount of outgoing spam remained the same as in the previous quarter. Only their shares changed. The biggest increase came from Russia, which ranked first, jumping by 5 p.p. to 23.52%. The shares of the remaining top-fivers did not fluctuate by more than one percentage point. Second-place Germany gained 11.01%, the US in third picked up 10.85%, France 6.69%, and China in fifth 6.33%.
The bottom half of the Top 10 changed more significantly. For instance, it said goodbye to Turkey, which this time took 11th place (1.73%). Sixth place was taken by the Netherlands (3.89%), seventh by Brazil (3.26%), eighth by Spain (2.52%), ninth by Japan (2.30%), and Poland (1.80%) rounds out the Top 10, up one position on last quarter.
Spam email size
Spam email size, Q2 2020 – Q3 2020 (download)
The downward trend in the number of very small emails continued in Q3 2020; their share decreased significantly — by 13.21 p.p. to 38.09%. The share of emails sized 20–50 KB grew by 12.45 p.p. to 28.20% of the total number of registered spam emails. But the number of emails 10–20 KB in size fell to 8.31% (–2.78 p.p.). Also lower was the share of spam messages sized 100–200 KB; this time their share was 1.57%.
Malicious attachments: malware families
Number of Mail Anti-Virus triggerings, Q2 2020 – Q3 2020 (download)
Throughout Q3 2020, our security solutions detected a total of 51,025,889 malicious email attachments, which is almost 8 million more than in the previous reporting period.
Top 10 malicious attachments in mail traffic, Q3 2020 (download)
The most widespread malware in Q3 mail traffic was assigned the verdict Trojan-PSW.MSIL.Agensla.gen (8.44%). In second place was Exploit.MSOffice.CVE-2017-11882.gen (5.67%), while Trojan.MSOffice.SAgent.gen (4.85%) came third.
Top 10 malware families in mail traffic, Q3 2020 (download)
This quarter’s most widespread malware family was Trojan-PSW.MSIL.Agensla (12.67%), having ranked second in the last reporting period. While last quarter’s leader Trojan.Win32.Agentb finished second (8.78%). Third place, as in the previous quarter, went to Exploit.MSOffice.CVE-2017-11882 (8.03%).
Countries targeted by malicious mailshots
Distribution of Mail Anti-Virus triggerings by country, Q3 2020 (download)
Since the beginning of the year, Spain has led the way by number of Mail Anti-Virus triggerings. In Q3, users in this country accounted for 7.76% of attacks. In second place this time was Germany (7.05%), knocking Russia (5.87%) into third.
Statistics: phishing
In Q3 2020, the Anti-Phishing system prevented 103,060,725 attempts to redirect users to fake pages, which is almost 3.2 million fewer than in Q2. The share of unique attacked users amounted to 7.67% of the total number of users of Kaspersky products
Attack geography
This time, the country with the largest proportion of users attacked by phishers was Mongolia (15.54%).
Geography of phishing attacks, Q3 2020 (download)
Israel (15.24%) lies close behind in second place, with France (12.57%) this time in third.
Top-level domains
The most popular top-level domain with phishers this quarter, as before, was COM (40.09% of the total number of top-level domains used in attacks). Silver went to XYZ (5.84%), and bronze to NET (3.00%). RU finished in fourth place (2.93%), and BUZZ in fifth (2.57%).
Top-level domains most popular with phishers, Q3 2020 (download)
Organizations under attack
The rating of attacks by phishers on different categories of organizations is based on detections by the Kaspersky Anti-Phishing component. This component detects pages with phishing content that the user tried to access by following email or web links, regardless of how the user got to the page: by clicking a link in a phishing email or in a message on a social network, or after being redirected by a malicious program. When the component is triggered, a banner is displayed in the browser warning the user about a potential threat.
As before, the Online Stores category absorbed the most phishing attacks, despite its share dropping slightly against Q2 2020 (by 0.20 p.p.) to 19.22%. Global Web Portals (14.48%) in second position and Banks (10.89%) in third were also non-movers.
Distribution of organizations subjected to phishing attacks by category, Q3 2020 (download)
Conclusion
The COVID-19 topic, which appeared in Q1 this year, is still in play for spammers and phishers. In our view, the so-called second wave could lead to a surge in mailings offering various coronavirus-related treatments. Moreover, against the backdrop of the worsening economic situation, we could see a rise in the number of scam mailings promising a big payout in exchange for a small upfront sum.
The average share of spam in global mail traffic (48.91%) this quarter decreased by 1.27 p.p. against the previous reporting period, while the number of attempted redirects totaled nearly 103 million.
First place in the list of spam-source countries in Q3 again went to Russia, with a share of 23.52%. Our security solutions blocked 51,025,889 malicious attachments; the most popular malware family in spam mailings was Trojan-PSW.MSIL.Agensla, with a 12.67% share of mail traffic.