The Australian Signals Directorate published a sobering The Commonwealth Cyber Security Posture in 2020 report on Thursday, with one of the bright spots being the use of scanning by the Australian Cyber Security Centre (ACSC).
Under its Cyber Hygiene Improvement Programs (CHIPs), the ACSC was able to identify vulnerable, internet-exposed MobileIron systems across Commonwealth, state and territory, and local governments.
“The ACSC notified all government entities operating vulnerable devices of the device details, the critical vulnerability and the urgent need to patch or otherwise mitigate the risk,” the report said.
“This timely and actionable information from the ACSC allowed some government entities to pre-empt adversary exploitation of their MobileIron devices, in one case by hours.”
The report said the 2020 MobileIron and Citrix vulnerabilities had some of the quickest turnarounds before exploitation attempts began to appear.
“Reporting showed adversaries attempting to exploit these vulnerabilities within days of proof-of-concept codes being publicly released,” it said.
“Organisations that cannot patch their internet-facing services in a very timely manner, especially legacy VPNs and websites, must improve their patching capability. Adopting software-as-a-service or platform-as-a-service cloud approaches to internet-facing services may assist.”
This is bad
Image: ASD
Elsewhere, the report said while in absolute terms the cyber posture of Commonwealth entities was improving, the shift was glacial in 2020.
For instance, the report said entities were improving application hardening, but only 12% of entities got better. Similarly, 10.5% were doing application control properly, and 9.5% more entities could say they were restricting admin privileges properly.
The blame for the slow pace was placed with entities continuing to use obsolete and unsupported operating systems and applications, not embracing cloud services, organisations not having fast or flexible modernisation strategies, a cyber skills shortage, and organisations continuing to “misunderstand, misinterpret and inconsistently” the Essential Eight.
In a government response tabled on Wednesday, the government is considering making the Essential Eight essential for its entities.
This is very, very bad
Image: ASD
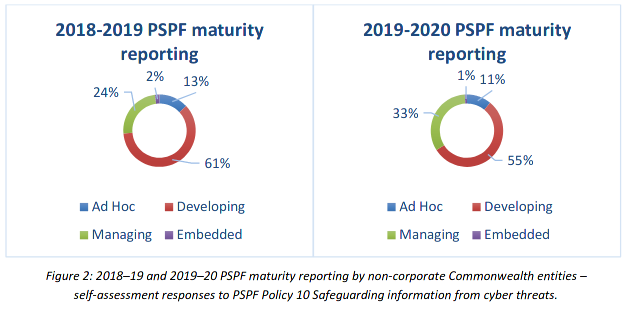
Restricting adherence to merely the Top Four of the Essential Eight showed 11% of organisations self-reported at the lowest level of compliance, followed by 55% at the second step of the four step system, with 33% at the third level, and only 1% being fully compliant.
The policy with the lowest level of maturity was “safeguarding information from cyber threats”.
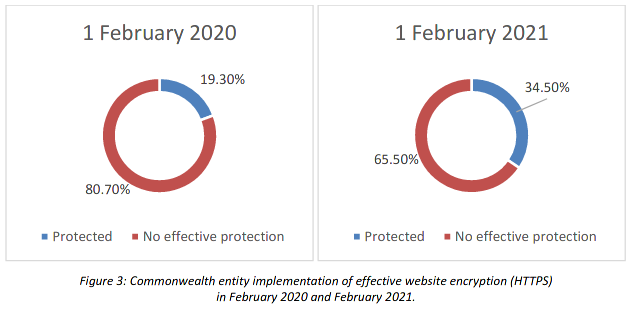
On the plus side, CHIPs is now able to track “cyber hygiene indicators” across 71,300 active Commonwealth government domains, an improvement of 54,300 domains in the year from February 2020, and covers the sites of 187 entities.
Across 2020, CHIPs gained the ability to scan for encrypted email use; whether government sites were running up-to-date software, displaying default websites or using expired certificates; scanning for critical vulnerabilities; and advising government entities at all levels on services they have open to the wider internet.
During the year, ACSC created a Protective Domain Name System that blocks domains associated with malware, ransomware, phishing attacks, and other malicious content.
“Under the pilot, the ACSC processed approximately 2 billion queries from eight Commonwealth entities over the period from April to December 2020 — and blocked 4683 unique malicious cyber threats, preventing over 150,000 threat events,” the report said.
“In 2021–22, the capability will be offered to all Commonwealth entities.”
Australia is so bad at cyber
Image: ASD
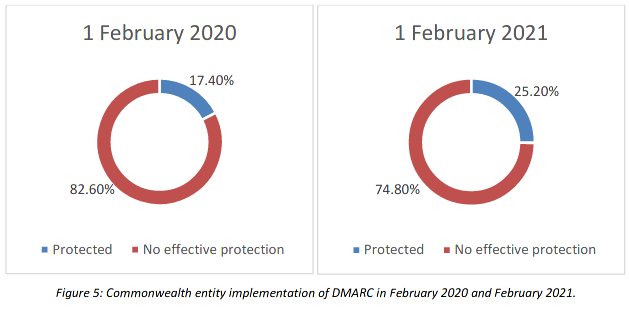
The report stated approximately one quarter of entities are now using DMARC to prevent email spoofing.
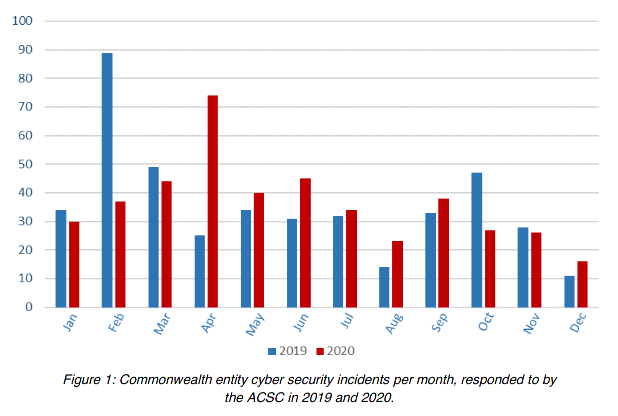
Across the year, ACSC said it responded to 434 cyber incidents, of which 46% were self-reported and the remainder were found through “ACSC investigations, reporting from international partners and third parties, and analysis of a variety of classified and open-source material”.
The next report will be handed to government in November 2022 and cover from January 2021 to June 2022. From 2023, the reports will focus on cyber posture across a single financial year.



