With the coronavirus (Covid-19) pandemic shutting down major parts of the global economy, governments are responding with massive stimulus packages aimed at supporting businesses and individuals. In the U.S. alone, the federal government is rolling out a $2 trillion package of Economic Impact Payments to help give the economy a shot in the arm and prevent a crash.
And of course, where there’s money, there will also be criminal activity. Hackers and threat actors want to cash in on the rush to get these vital payments and fill their own pockets at the expense of others. To do this, they are evolving the scam and phishing techniques that they have been using successfully since the start of the pandemic in January. Google recently reported that in just one week from 6 to 13 April, it saw more than 18 million daily malware and phishing emails related to Covid-19 scams – and that’s in addition to the 240 million daily spam messages it sees related to coronavirus.
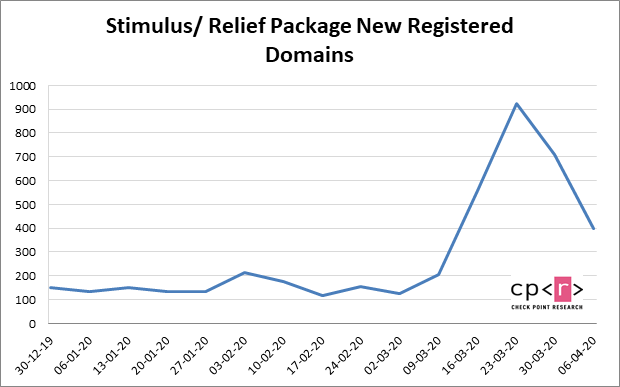
Our researchers have found that since January, a variety of domains related to coronavirus-related stimulus or relief packages have been registered globally. A total of 4,305 domains relating to new stimulus/relief packages have been registered:
- In March 2020 – a total of 2081 new domains were registered (38 malicious; 583 suspicious)
- In the first week of April – 473 were registered (18 malicious, 73 suspicious)
- We’ve also seen a major increase in the week starting March 16 during which the American government proposed the stimulus package to taxpayers. The number of new domains registered that week was 3.5 times higher compared to the average of previous weeks
These scam websites use the news of the coronavirus (Covid-19) financial incentives, and fears about Coronavirus to try and trick people into using the websites or clicking on links. Users that visit these malicious domains instead of the official Government websites risk having their personal information stolen and exposed, or payment theft and fraud.
Examples of a targeted email to a specific victim targeting a US company (name of the victim and his mail in each one of the black marks):
As well as the example detailed below, emails with malicious attachments were sent with subjects related to the stimulus such as “RE: UN COVID-19 Stimulus” (distributing the AgentTesla malware) and “COVID-19 Payment“ distributing the Zeus Sphinx trojan.
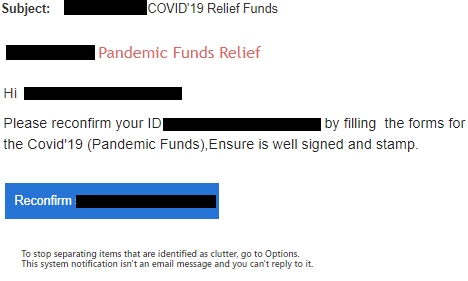
When clicking on the Reconfirm button the victim is directed to a phishing login page:
Coronavirus related cyber-attacks
Ninety-four percent of coronavirus-related attacks during the past 2 weeks were phishing attacks, while 3% were mobile attacks (either via dedicated mobile malware or via malicious activity carried out on a mobile device).
We define coronavirus-related attacks as those that involve
- websites with “corona”/”covid” in its domain
- files with “Corona” related file names
- files that have been distributed with coronavirus-related subjects in their email
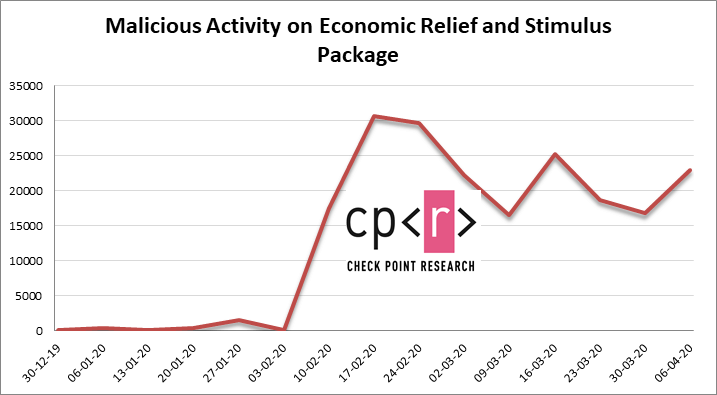
We have also seen a huge increase in the number of attacks, to an average of 14,000 a day, which is six times the average number of daily attacks when compared to the previous two weeks. And over the past week from 7th April, the average number of daily attacks increased sharply to 20,000.
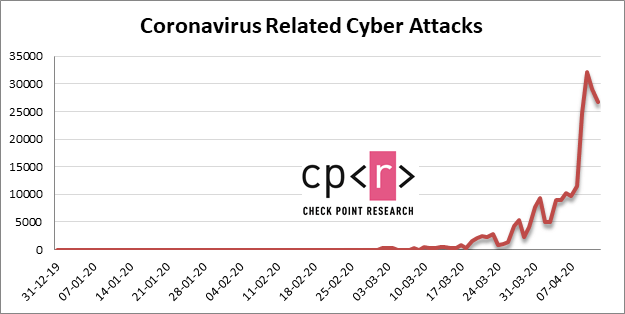
The graph represents all coronavirus-related attacks that have been detected by Check Point’s different Threat Prevention technologies across networks, endpoints and mobile devices.
Coronavirus-related malicious domains
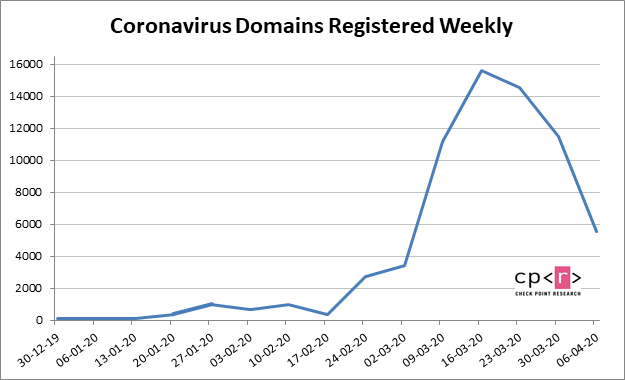
As we previously reported, since mid-February we have seen an escalation in the number of coronavirus-related domains being registered. In the past two weeks (since our last update on April 2), almost 17,000 new coronavirus-related domains had been registered (16,989 to be exact). 2% of those domains were found to be malicious, and another 21% suspicious. In all, there have been 68,000 coronavirus-related domains registered since the beginning of the outbreak in January 2020.
Staying protected against phishing attacks
Phishing is the starting point for the majority of cyber-attacks. To stay safe, remember these golden rules:
- Beware of lookalike domains, spelling errors in emails or websites, and unfamiliar email senders.
- Be cautious with files received via email from unknown senders, especially if they prompt for a certain action you would not usually do.
- Ensure you are ordering goods from an authentic source. One way to do this is NOT to click on promotional links in emails, and instead, Google your desired retailer and click the link from the Google results page.
- Beware of “special” offers. “An exclusive cure for coronavirus for $150” is usually not a reliable or trustworthy purchase opportunity. At this point of time there is no cure for the coronavirus and even if there was, it definitely would not be offered to you via an email.
- Make sure you do not reuse passwords between different applications and accounts.
Source : Check Point Software Technologies