Zero Trust has become a widely adopted cybersecurity strategy, and organizations are learning to operate under the assumption that no user, endpoint, workload, application or content can be trusted within their networks, no matter what’s been previously checked or what will be checked later on. In other words, each device, application and microservice must be responsible for its own security.
There’s a learning curve, however, to understanding how to apply that principle throughout your infrastructure. In the case of cloud native technologies, infrastructure and development processes often don’t look the same as in traditional environments. The way we apply Zero Trust must shift as well. In constantly changing cloud environments, Zero Trust microsegmentation is a technique that can help enforce cloud security policies that follow Zero Trust best practices.
Developers and DevOps teams continue to use cloud native technologies like microservices and containers to scale development and speed up releases, along with multi-cloud architectures to optimize efficiency. However, it’s these same core components of cloud native development that are causing fundamental shifts in the way network security policies are administered in the cloud. Zero Trust microsegmentation can help solve issues where environments are constantly changing and the IP addresses that were traditionally used for managing and defining security policies are no longer sufficient.
Why Cloud Security Policies Can’t Be Based on IP Addresses
Cloud native development can present a challenge to traditional enterprise policies, partially due to the nature of constant change within the environments. Cloud workloads move across locations, and instances within an application can scale dynamically as demands fluctuate and containers come and go in seconds – making validation a serious concern.
In these environments, the IP-based security that many enterprises are used to can quickly become unmanageable. Hybrid and multi-cloud environments introduce shifting IP domains as containerized workloads can be replicated, rescheduled and rehosted within the scope of an hour. And microservices are exposed through APIs accessible via HTTP/gRPC, making IP address irrelevant. In order to achieve end-to-end visibility, administrators would have to stitch together IP flows across the multitude of environments, which becomes unworkable at scale.
Because IP addresses are no longer as persistent as they once were, they cannot be relied upon to accurately identify workloads in the cloud, thereby making them unusable for security policies following Zero Trust best practices.
Identity-Based Microsegmentation
Identity-Based Microsegmentation in Prisma Cloud gives users the ability to base security policies on strong, machine-generated identity for individual workloads instead of broad IP addresses. This makes it possible to track a workload as it moves through your environment, even if IP addresses and other traditional identifiers change. Development risk posture is improved while managing the needs of dynamic cloud native environments.
Once workload identities are assigned, Prisma Cloud can automatically discover and learn application communication behaviors inside and across clouds. These flows can then be monitored in real time using a visualized map of the network.
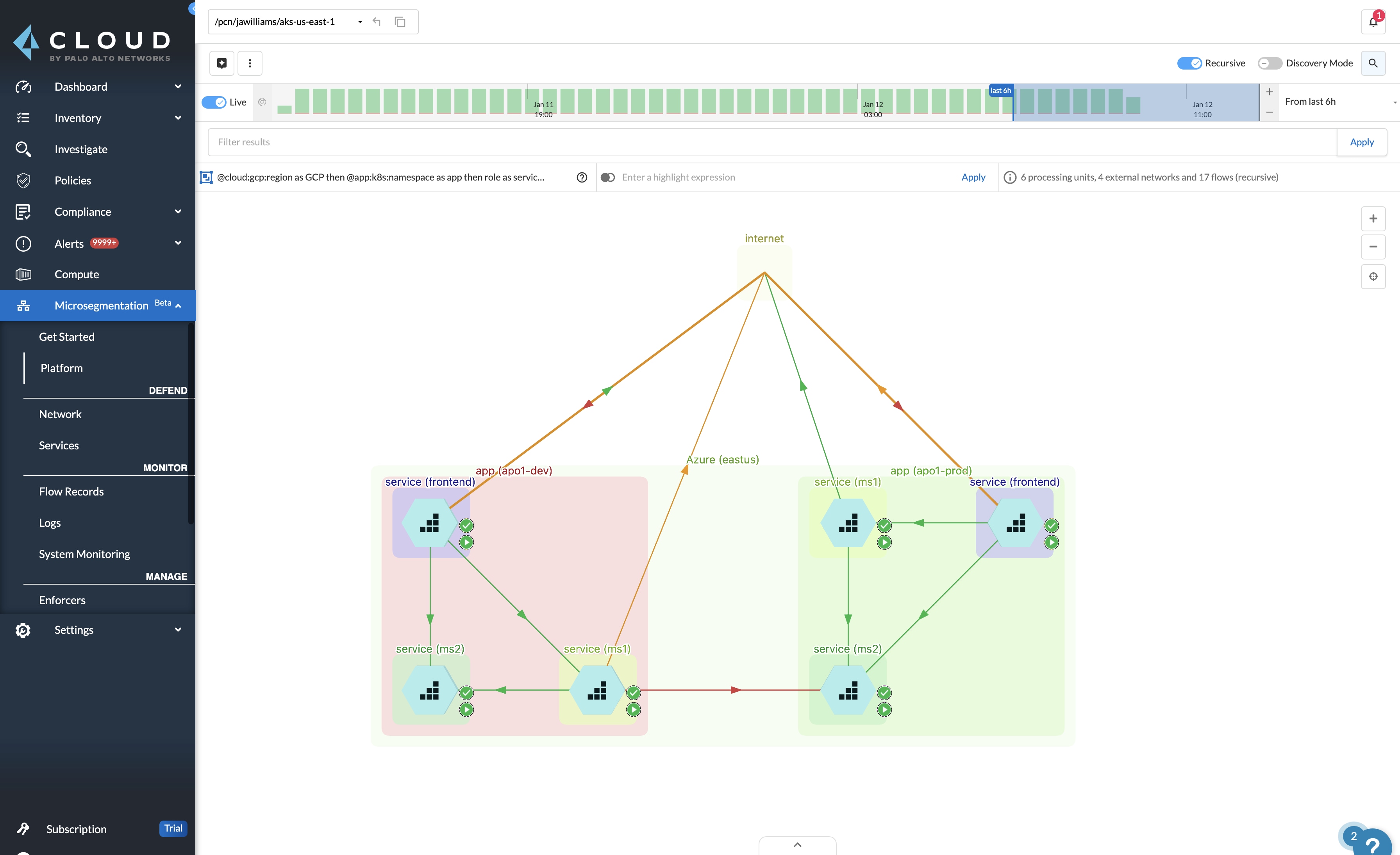
Users can set policies to authenticate and authorize connection requests among these generated identities, and they can automatically deny unknown requests. Compliance teams, for example, can create policies to isolate systems that may be subject to specific regulations.
Microsegmentation for Zero Trust
Microsegmentation gives organizations a way to implement Zero Trust best practices for cloud native application development. A trusted identity can be used for security policy enforcement while allowing the seamless use of technology like containers and microservices. You can learn more in our e-book, “Identity-Powered Microsegmentation with Prisma Cloud.”
Microsegmentation is just one aspect of an enterprise Zero Trust strategy. Watch as Palo Alto Networks Founder and CTO Nir Zuk explains how it all fits together. And be sure to check out the rest of the blogs in our Zero Trust series.
[embedded content]
By Palo Alto Networks Source Link




















