On May 27, 2021, Microsoft reported a wide scale spear phishing campaign attributed to APT29, specifically the associated group Nobelium, the same threat actor responsible for the SolarWinds campaign named SolarStorm. This attack had a wide range of targets for an advanced persistent threat (APT) spear phishing campaign with 3,000 email accounts targeted at 150 organizations. This recent wave of cyberattacks by the SolarWinds-linked Nobelium threat actor has shown the world the sheer level of sophistication behind these increasingly powerful attacks on targeted entities. The threat actors are well-organized with a clear game plan and seem to have invested significant time, energy and effort on experimenting with available techniques, tools and technologies to hit their targets. Threat actors have clearly upped the game in cyberspace. Given the level of sophistication and planning around these attacks by the adversaries, it is time organizations level up their incident response speed and bring threat intel management and post intrusion response and remediation capabilities to their SecOps and threat hunting teams. To help, we’ve created a Cortex XSOAR playbook that can automate many of the steps needed to respond to this attack by Nobelium.
What’s New About the APT29 Spear Phishing Attack?
Phishing attacks and campaigns are not new. Phishing has been the number one attack vector for a long time, and organizations deal with phishing incidents on a daily basis. What is new with this spear phishing campaign? The modus operandi of the threat actor has changed. The Nobelium threat actor managed to insert a well-crafted playbook into its malicious operations to gain access to legitimate commercial mass mailing services. The threat actor managed to take over legitimate email marketing accounts and use the legitimate tool’s automated mass-mailing service to hit their targets with spear phishing emails. Recipients understandably tend to trust emails that appear to have come from a trusted source like the U.S. federal agency (USAID in the case of the recent attacks).
How Cortex XSOAR Can Help
Our mission has been to help our customers automate security operations as much as possible – a key part of staying ahead of today’s automated attackers. To help with this, we provide playbooks for specific types of response and maintain an ecosystem where others can contribute playbooks as well – and we advise our customers to add our playbooks to their SecOps process to automate what they can.
For this attack and many others, organizations can leverage the power of automation with Cortex XSOAR to help speed up the discovery and remediation of compromised hosts within the network. XSOAR’s automated playbooks help in unifying threat feed ingestion, indicator enrichment and incident management workflows, helping your team to respond to such attacks at machine speed.
Cortex XSOAR’s security research team has released the NOBELIUM – Wide Scale APT29 Spear-Phishing playbook to help customers bring the required threat hunting and incident response capabilities to SecOps. The new playbook is focused on tackling phishing campaigns from the Nobelium threat actor and takes the following approach to insert automation into the response procedures.
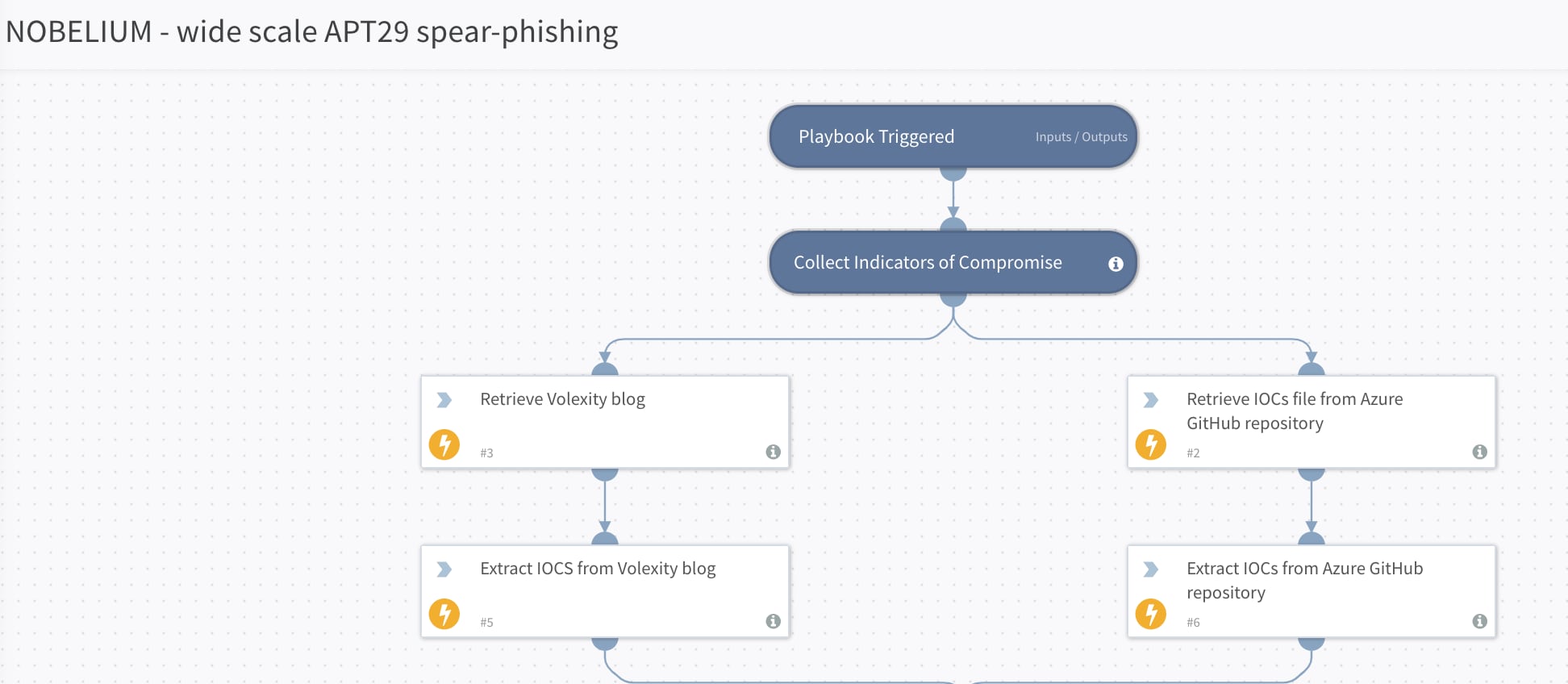
Step 1: Collect indicators of compromise (IOCs) from reliable sources to be used in your threat hunting process. The NOBELIUM – Wide Scale APT29 Spear-Phishing response playbook collects indicators of compromise from several different trusted sources automatically.
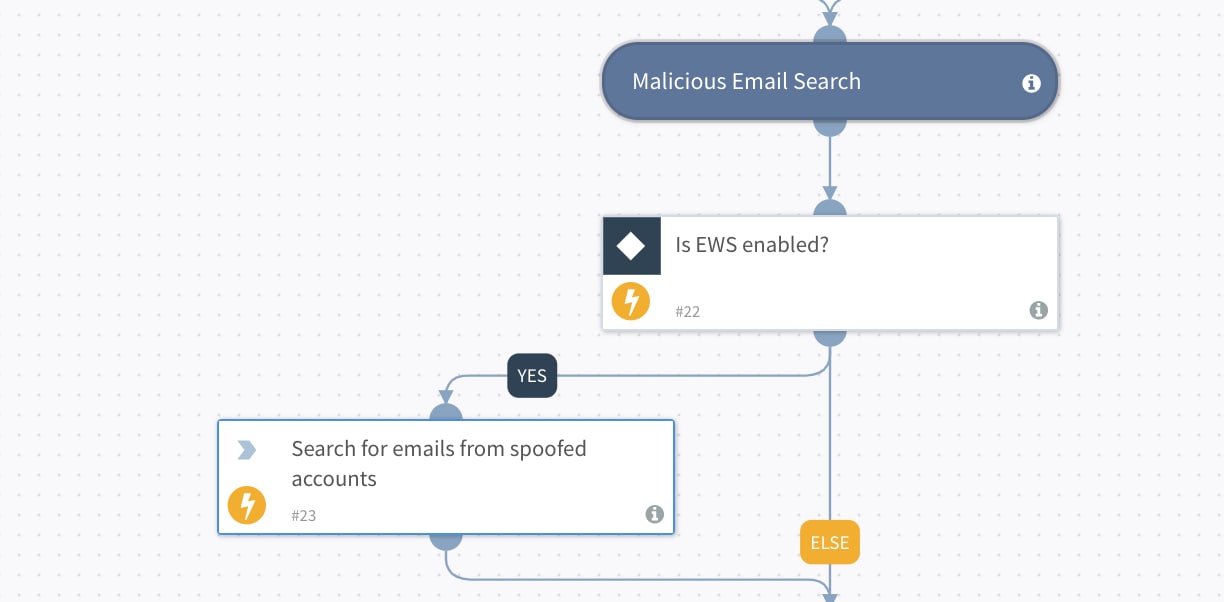
Step 2: Look for phishing emails in the mailbox. The playbook action searches for emails from spoofed accounts. Cortex XSOAR has out-of-the-box integrations with several mailbox vendors.
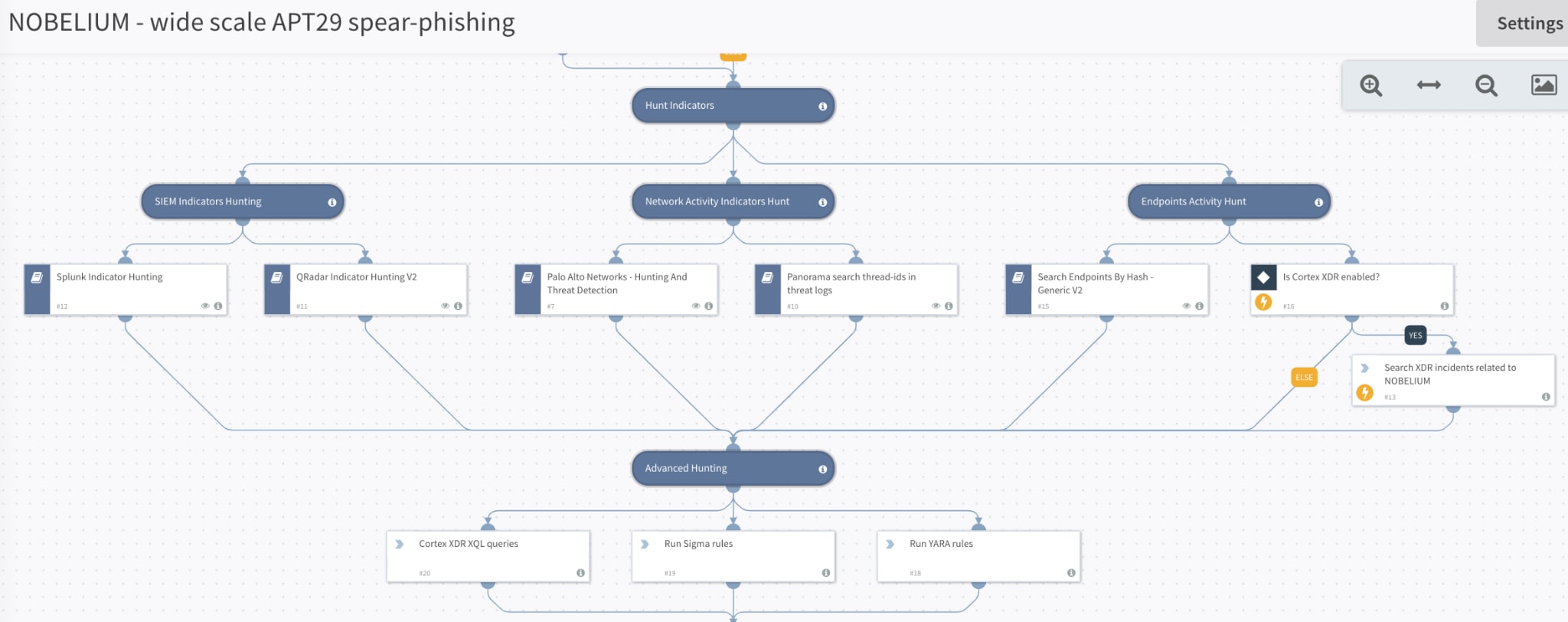
Step 3: The most time-consuming part of the incident response process is performing a rigorous hunt to identify malicious activity. This may involve querying SIEMs, EDR, Firewalls or XDR to detect malicious hashes, network activity and compromised hosts. All these actions are covered by the playbook and have been automated for quick insertion into the threat hunting process for better speed and accuracy.
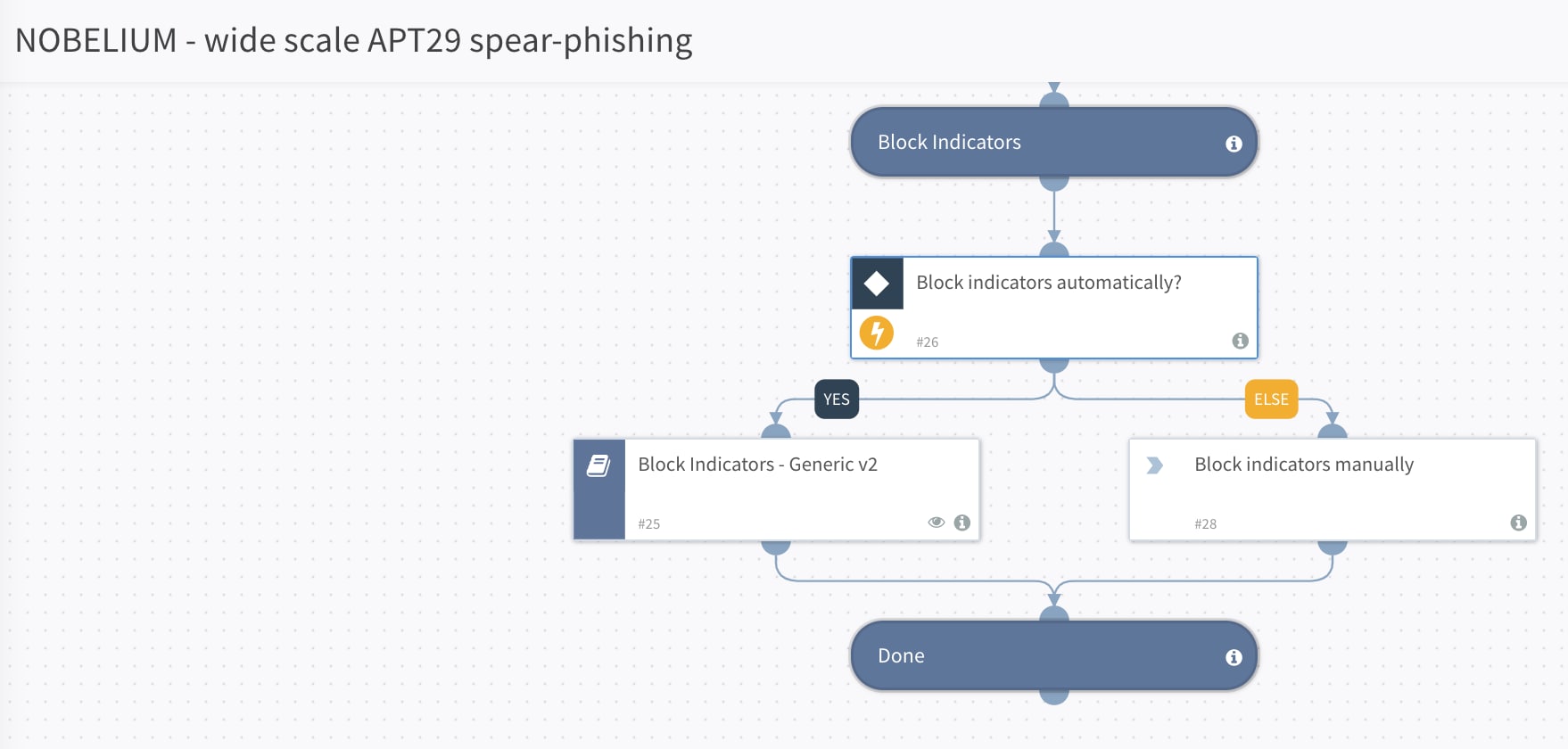
Step 4: Block identified indicators on the third-party enforcement points.
Additionally, SecOps and threat hunting teams can refer to the Canvas section of the phishing incident investigation to quickly identify relationships between different indicators, as shown below. All the indicators related to a specific spear phishing email would appear on the Canvas, providing for quick visual correlation between the spear phishing incident and the related indicators. Analysts can readily view the reputation of the indicators in the same section. This drastically reduces time spent in investigating phishing incidents to extract indicators and identify reputations from multiple different sources.
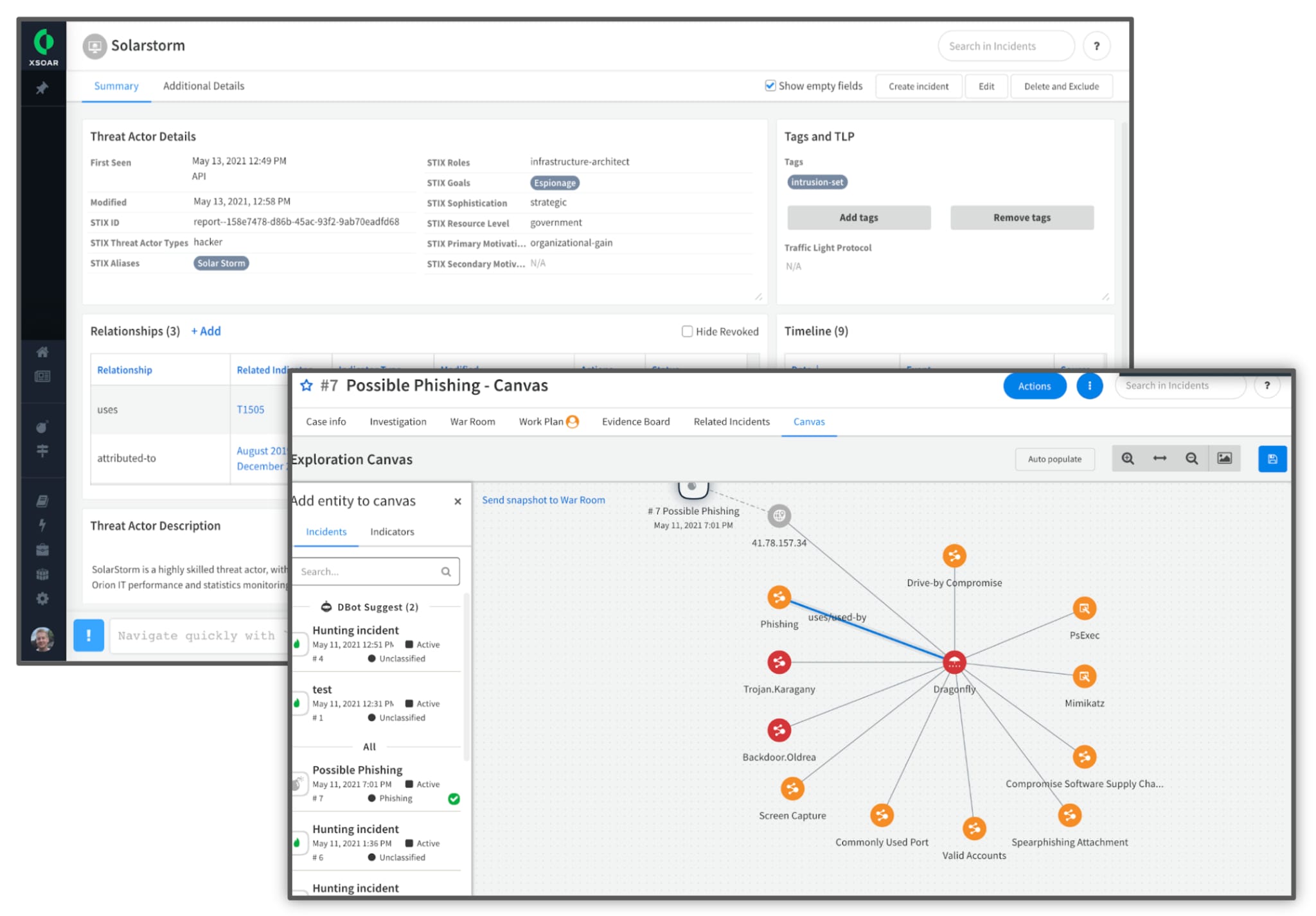
How to Find the NOBELIUM – Wide Scale APT29 Spear-Phishing Playbook
NOBELIUM – Wide Scale APT29 Spear-Phishing is part of the Rapid Breach Response content pack available for download from the Cortex XSOAR Marketplace. Rapid Breach Response is a collection of playbooks developed by our security research teams in response to high-profile breaches and attacks, such as SolarStorm.
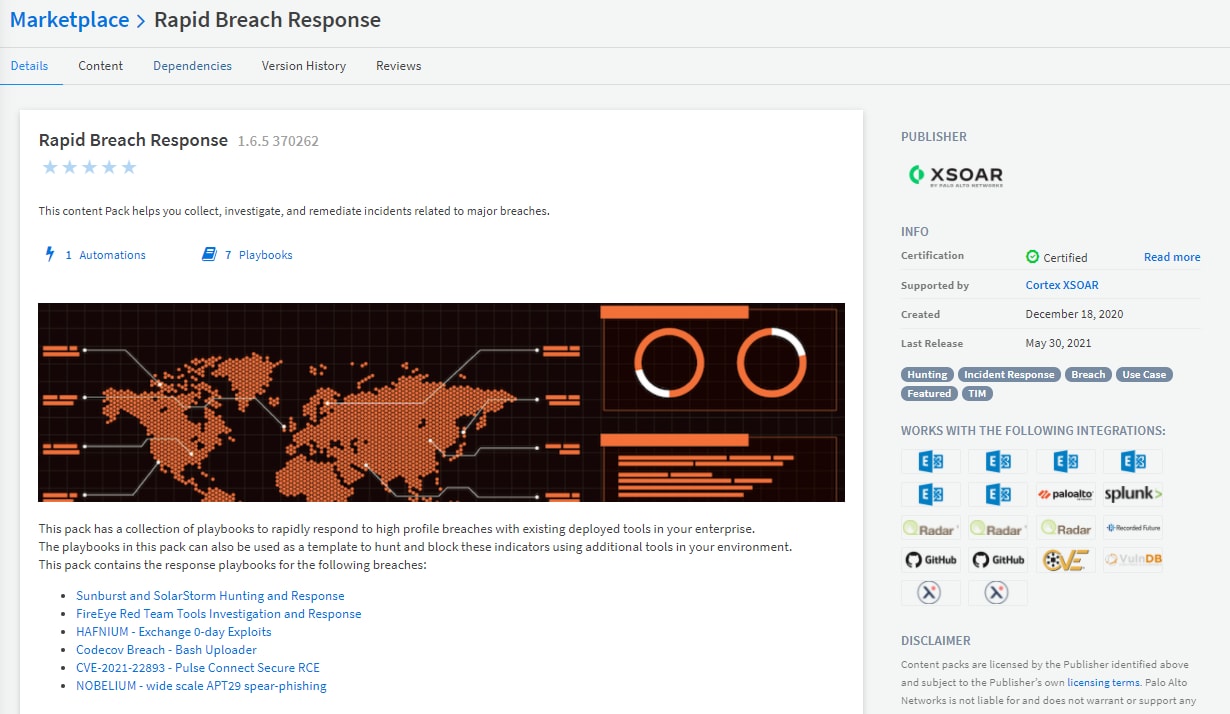
With the help of this Cortex XSOAR playbook, your SecOps and threat intel teams can save many hours of manual labor chasing down compromised hosts and trying to piece together disparate sources of information from multiple tools. Cortex XSOAR can automate the whole process of data enrichment and threat hunting by orchestrating across SIEMs, firewalls, email security, endpoint security and threat intelligence sources so you can quickly shut down Nobelium and limit its impact on your network. You can find the Rapid Breach Response content pack playbooks in our Cortex XSOAR Marketplace.
Don’t have Cortex XSOAR yet? Try the free community edition today.
Additional Resources
Hunting for APT29 Spear Phishing Using XDR
Note: This is an active incident. We will post more details here as they become available.
By Palo Alto Networks Source Link






















