Although the Flash Player app formally reached its end of life on December 31, 2020, Adobe has allowed a local Chinese company to continue distributing Flash inside China, where the application still remains a large part of the local IT ecosystem and is broadly used across both the public and private sectors.
Currently, this Chinese version of the old Flash Player app is available only via flash.cn, a website managed by a company named Zhong Cheng Network, the only entity authorized by Adobe to distribute Flash inside China.
But in a report published earlier this month, security firm Minerva Labs said its security products picked up multiple security alerts linked to this Chinese Flash Player version.
During subsequent analysis, researchers found that the app was indeed installing a valid version of Flash but also downloading and running additional payloads.
More precisely, the app was downloading and running nt.dll, a file that was loaded inside the FlashHelperService.exe process and which proceed to open a new browser window at regular intervals, showing various ad- and popup-heavy sites.
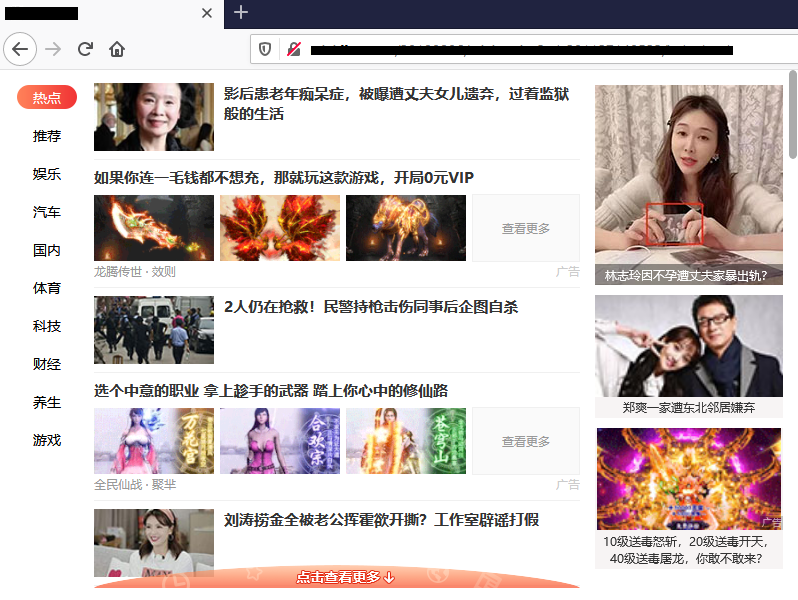
The spammy behavior obviously didn’t go unnoticed. Both regular users and other security firms noticed it as well.
Users complaining that Flash has now started showing popups have been spotted on the Adobe support forum, several local blogs, and in many other places.
Furthermore, besides Minerva Labs, other security firms have also started picking up suspicious activity related to the FlashHelperService.exe. Cisco Talos ranked this process as its most widely detected threat for the weeks ending on January 14 and January 21, and the file also ranked in its Top 10 on the weeks ending on January 7, February 11, and February 18.
This particular threat doesn’t impact western users since the Flash version they download from flash.cn won’t work on systems outside China, but in light of Minerva’s report, they shouldn’t even try to test it, as this may lead to installing adware and compromising the security of their systems/networks.






















