Every fifth business executive prefers not to flag lack of understanding when discussing cybersecurity issues. A recent Kaspersky study also reveals one in ten C-level managers have never heard of threats such as Botnet, APT and Zero-Day exploit. The same proportion appeared to be unfamiliar with cyber security concepts like DecSecOps, ZeroTrust, SOC and Pentesting.
According to a PwC’s study, while backing cybersecurity in every business decision has already become the norm in every other company, more than half of executives lack confidence that their cyber spending is being allocated to the most significant risks their organization is facing. Kaspersky conducted their own research to help IT and C-level find common ground and explore the root of their misunderstandings.
The Kaspersky poll indicates that C-suite sometimes struggle to understand their IT security peers and are not always ready to show their confusion. Thus, 22% of non-IT executives say they would not feel comfortable flagging that they don’t understand something during a meeting with IT and IT security. Although most of them hide their confusion because they prefer to clarify everything after the meeting or choose to figure everything out by themselves, 37% don’t ask additional questions because they don’t believe the IT peers will be able to explain it in a clear way. Almost three-in ten also feel embarrassed revealing they don’t understand the topic and 33% don’t want to look ignorant in front of IT colleagues.
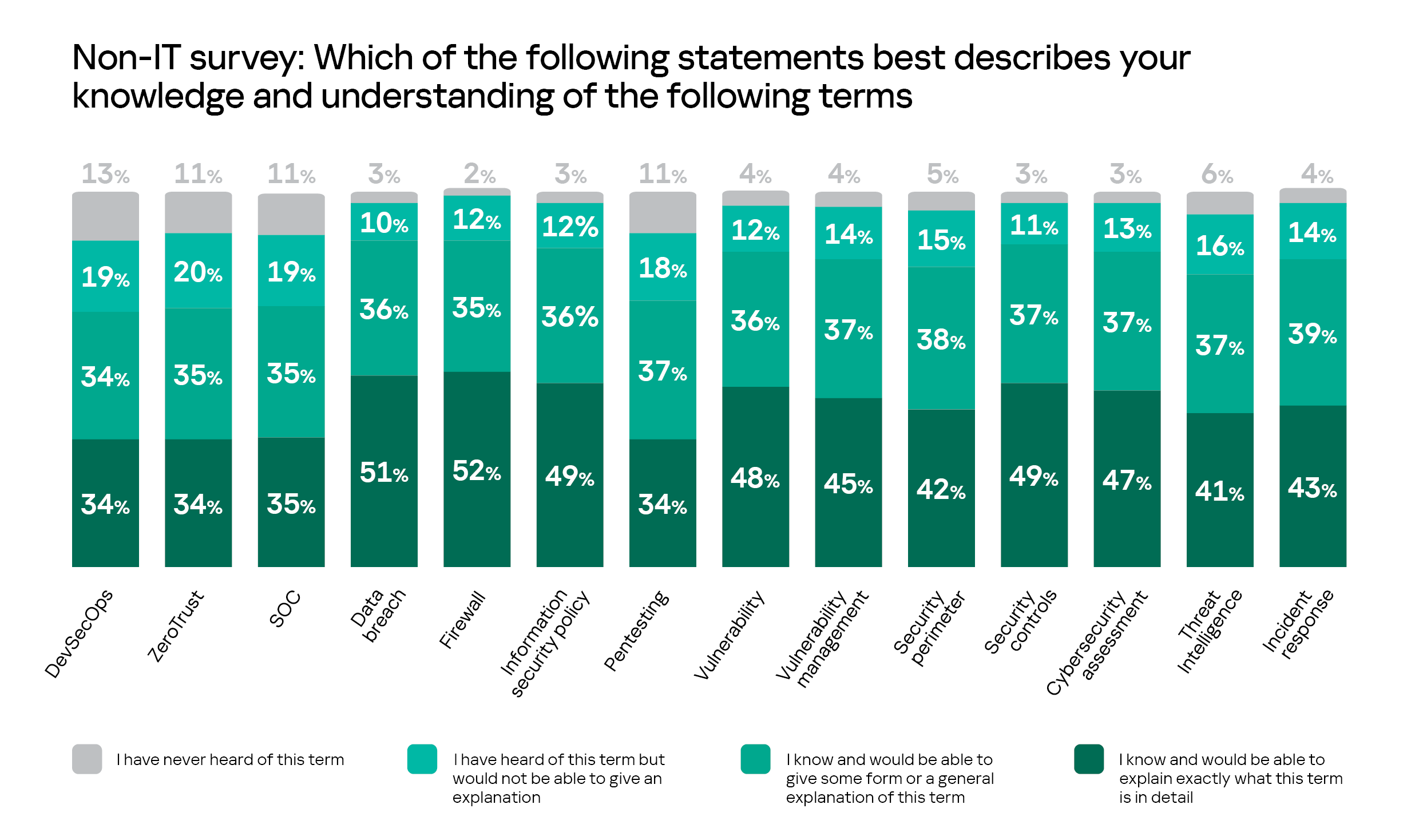
Also, even though all surveyed top-managers regularly discuss security related issues with IT security managers more than one-in-ten respondents have never heard of threats such as Botnet (12%), APT (11%) and Zero-Day exploit (11%). At the same time Spyware, Malware, Trojan and Phishing appeared to be more familiar for top-mangers.

More than one-in-ten top managers admit they have never heard of cybersecurity terms like DecSecOps (13%), ZeroTrust (11%), SOC (11%) and Pentesting (11%).
“Non-IT top management do not have to be experts in complex cybersecurity terminology and concepts and IT security executives should keep this in mind when communicating with the board “. – comments Sergey Zhuykov, Solution Architect at Kaspersky. “To establish efficient cooperation CISO should be able to focus C-level attention precisely on meaningful details and clearly explain what exactly the company is doing to minimize cybersecurity risks. In addition to communicating clear metrics to stakeholders, this approach requires offering solutions instead of problems”.
To ease the communication between IT security and business functions within the company, Kaspersky recommends the following:
- IT security should be positioned as a driver for growth and innovation in the organization. To achieve this the IT security team should move away from prohibitive tactics and rather explain how the business can achieve its goals while mitigating cybersecurity risks.
- CISO should actively engage in operational activities and build relationships with the company’s stakeholders. While fewer than 20% of CISOs have established partnerships with key executives in sales, finance, and marketing, it is hard for them to stay abreast of the needs of the business.
- When communicating with the board, use arguments based on an overview of threats by experts, your company’s attack status and best practices.
- Explain the board what the main responsibilities of IT security team are. If possible, provide them with an opportunity to walk in a CISO’s shoes to get insights on the most relevant IT security challenges.
- Allocate cybersecurity investments in tools with proven efficacy and ROI. This means tools that lower the level of false positives, and reduce times of attack detection, the time spent per case and other metrics are important to any IT security team.
The full report and more insights on communications issues between C-level and IT security managers are available via the link.























