By Radware | Source
As network architectures evolve to support 5G, it will leave security vulnerabilities if cybersecurity isn’t prioritized and integrated into a 5G deployment from the get-go to provide a secure environment that safeguards customers’ data and devices.
Cybersecurity for 5G shouldn’t be viewed as an additional operational cost, but rather as a business opportunity/competitive differentiator that is integrated throughout the overall architecture. Just as personal data has become a commodity in today’s world, carriers will need the right security solution to keep data secure while improving the customer experience via a mix of availability and security.
Network Security Impacts
Current carrier networks aren’t capable of handling the security requirements of 5G networks. The same capabilities that allow 5G networks to deliver lightning-fast connectivity also allow hackers to execute larger, higher volume cyberattacks. Network security managers already face difficulty in predicting and preparing for today’s attacks,
becoming easy prey in the 5G universe.
Network infrastructure for 5G networks necessitates tightknit cybersecurity, as any network opening can result in a massive data breach or severe volumetric attacks. When combined with internet of things (IoT) devices, unprepared SOC teams can be overwhelmed by unprecedented threats.
For example, 5G shifts the current network paradigm by redefining what “fast-paced” will be. The digital and virtual transformation utilizes more cloud applications dependent on various APIs, multiplying the complexity of interconnected devices that rely on quick speeds, such as smartphones and IoT devices. This becomes a key issue for 5G network managers because of the increased number of potential vulnerabilities if they are not properly protected.
A New Network Build
For 5G networks to thrive, the underlying architecture will be distributed in the cloud and will no longer be dependent on dedicated appliances. The corresponding implementation and deployment of the carriers’ networks will evolve to expand capacity, reduce latency, lower costs and reduce necessary power requirements.
To reinforce this open environment, organizations using 5G will have to virtualize their network functions, resulting in less control over the physical elements of the networks in exchange for the 5G benefits in infrastructure. Services are also no longer restricted to service providers’ networks and can originate from external network domains. This means that services can rely on physically closer, virtualized network resources to the connected device for more efficient delivery.
5G will utilize the concept of network slicing to enable service providers to “slice” portions of a spectrum to offer specialized services for specific device types, all the while remaining in the same physical infrastructure.
Protecting the 5G Infrastructure
Having a secure network architecture from the start is crucial. Security Magazine has highlighted research that found that hackers attack every 39 seconds, leaving organizations with virtually no time to respond. From the ground up, cybersecurity is critical for surviving and thriving in the new threat landscape targeting 5G networks and service providers.
[You may also like: Is 5G the Security Silver Bullet for System Integrators in the West?]
5G incorporates tools that better support its agile structure. These same instruments, however, simultaneously increase the number of potential vulnerabilities and threats if implemented incorrectly, thereby increasing the threat landscape exponentially. There are four primary “directions” from which a 5G mobile network can be breached:
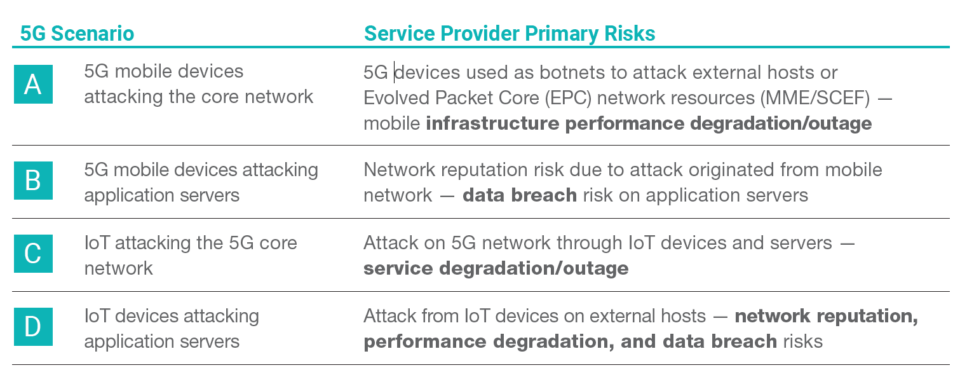
What’s At Stake
Regardless of the types of attacks that they experience, service providers will always be held to the highest standard of expectation to provide secure experiences that protect their customers while maintaining service availability. With each attack, service providers risk customer loss, brand reputation, lost profits and, at the worst, costly governmental involvement and resulting investigations and lawsuits.
In addition to the aforementioned costs, the costs of implementing or overhauling cybersecurity systems after 5G networks have been implemented can be high. The onus is on service providers to do their due diligence and integrate cybersecurity into any network architectures, starting with the foundation.

























