Researchers have explored how the coronavirus pandemic has affected the cybercrime space and the common trends found between COVID-related schemes.
In a new Trend Micro report viewed by ZDNet, the team explored the increased dependence on online services prompted by the pandemic — and how threat actors are trying to cash in.
Due to physical business and office closures, lockdowns, and stay-at-home orders, companies trying to survive have needed to either ramp up their online services or create them from scratch — ranging from e-commerce shops to delivery services.
Government and medical organizations, too, suddenly had to expand their online presence in order to offer telehealth services and vaccine appintment registration.
As new platforms spring up to cater to consumer economic and medical needs, threat actors are pivoting to campaigns designed to impersonate legitimate sources in the hopes of malware deployment and data theft.
“Cybercriminals usually impersonate known entities and create convincing replicas of email, website, or apps from legitimate sources,” the researchers note. “Due to this, users might have a harder time identifying legitimate platforms from malicious ones. This might be especially true for those who are using online systems heavily for the first time, such as many of the elderly.”
Misinformation, too, is of concern, with companies including Facebook and Twitter introducing strike systems for prolific spreaders of coronavirus-based fake news and data.
Now, with vaccine programs underway worldwide, COVID-19 vaccines are being used as the latest social engineering lures.
According to recent Trend Micro data, over the past few months, there has been an uptick in spam campaigns using the coronavirus vaccine as a subject to spread Emotet, Fareit, Agent Tesla, and Remcos across the US, Italy, and Germany, alongside other countries.
An Emotet Trojan campaign, tracked across January, used a variety of email lures including Daily COVID reporting.doc, DAILY COVID-19 Information.doc, NQ29526013I_COVID-19_SARS-CoV-2.doc, and GJ-5679 Medical report Covid-19.doc.
An analysis of over 80 linked samples also revealed vaccine-related email subjects such as COVID-19 Vaccine Survey and COVID-19 Vaccine Clinic with Walgreens To Do Now.
This particular campaign used roughly 100 command-and-control (C2) servers before being taken down by law enforcement.
The Fareit Trojan campaign also uses COVID-19 vaccines as bait and messages have been sent fraudulently under the name of the World Health Organization (WHO). Subjects included Corona-virus(COVID-19), Common vaccine, Corona-Virus Disease (COVID-19) Pandemic Vaccine Released, and Latest vaccine release for Corona-virus(COVID-19).
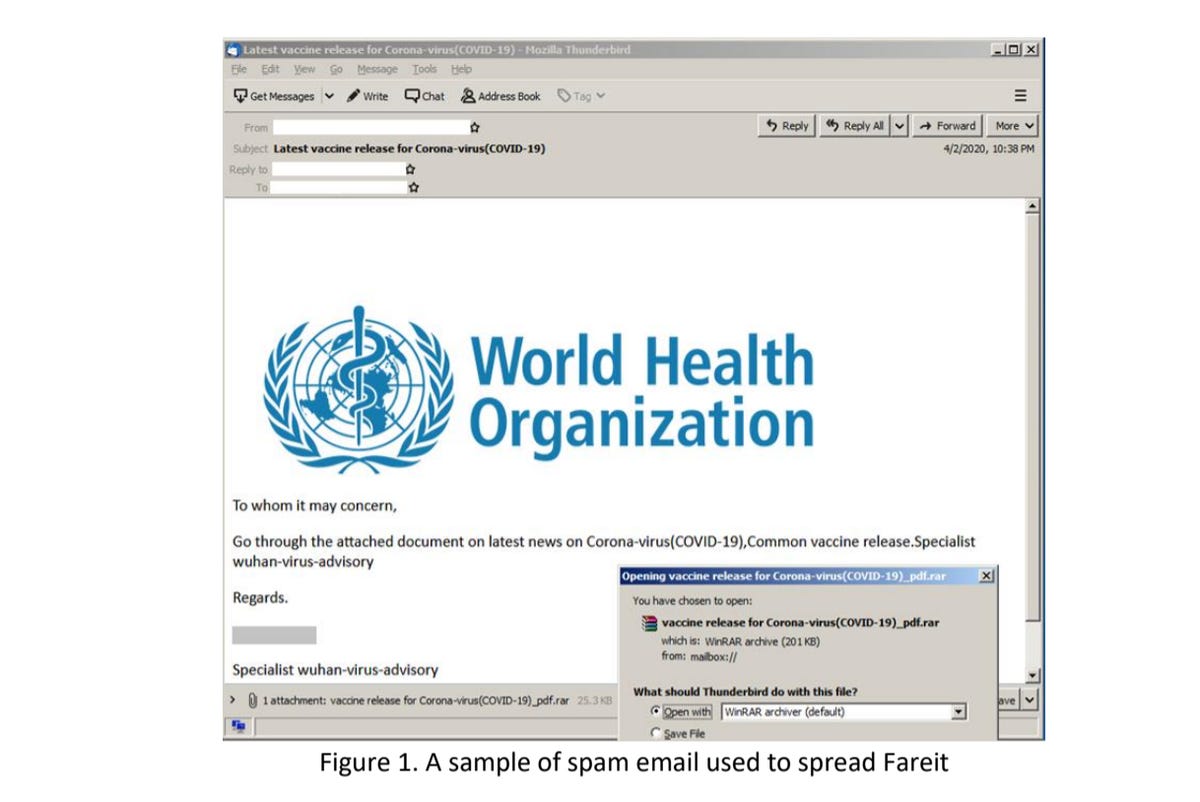
Malicious attachments, designed to deploy the information-stealing malware, were packaged up as .arj and .rare file formats with names including Corona-virus vaccine.arj, vaccine release for Corona-virus(COVID-19)_pdf.rar, and COVID-19 VACCINE SAMPLES.arj.
Lokibot, Agent Tesla, Formbook, Remcos, and Nanocore have also been spread through coronavirus-related scams, and in some samples detected, the same phishing tactics have been applied to spread the Android Anubis malware.
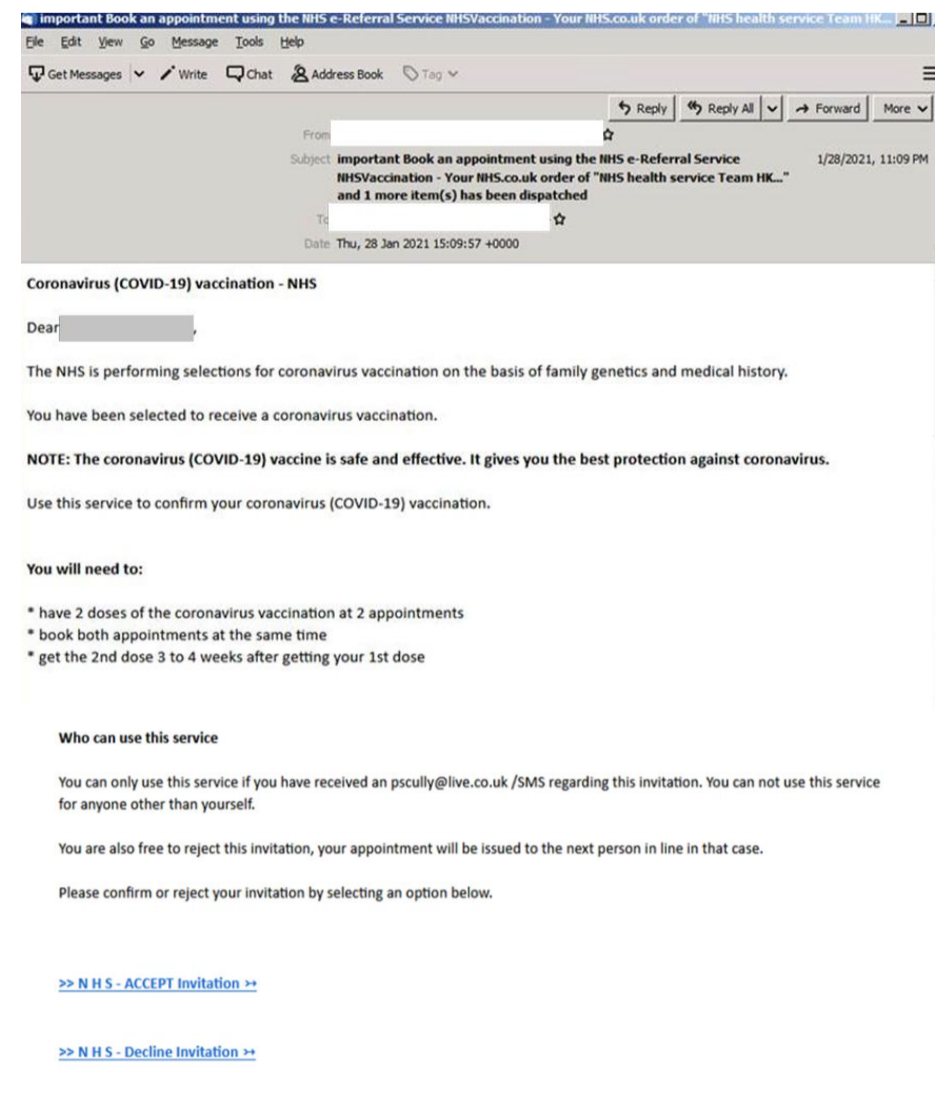
The European Medicines Agency (EMA) was targeted last year, with confidential, internal emails stolen and tampered with to undermine vaccine development efforts, and now, the UK’s National Health Service (NHS) is being impersonated in a phishing scheme which ‘invites’ recipients to book a vaccine.
As one of the leading countries, at present, in rolling out vaccines, this lure may be particularly successful as citizens are either waiting to be called up or are waiting for their invitation for a second jab.
“The email entices a user to confirm that they accept the invitation for vaccination,” the report notes. “Whether the “accept” or “disregard” button of the invitation is clicked, the email redirects to a landing page. This page displays a form requesting the user’s full name, birth date, address, and mobile number.”
A similar scam has been traced in Mexico, in which a website is being used to mimic a legitimate vaccine lab, El Chopo, to harvest victim data by pretending to be a service for vaccine cards and appointment scheduling.

With many vaccines requiring cold storage, other campaigns are focused on businesses and trying to profit from the need to establish cold supply chain procedures. In September, for example, the team tracked a scam requesting quotes for Unicef for Gavi’s Cold Chain Equipment Optimization Platform (CCEOP). Email attachments were linked to phishing and data-stealing domains.
SMS messages are also being used as an attack vector, including messages ranging from vaccine ‘eligibility’ checks, registration, COVID-19 relief payments, appointment booking, and offers of health ‘supplements’ to fight the virus.
Trend Micro’s report also notes an uptick in the registration of malicious domains concerning the pandemic. Roughly 75,000 malicious domains have been found that relate to ‘covid,’ however, a transition is now underway that is changing ‘covid’ to ‘vaccine’.
Many of these malicious domains are attempting to mimic legitimate pharmaceutical organizations and brand names, including BioNTech, Gam-COVID-Vac, and Sputnik.
While all this is taking place in the clear web, it should be noted that scam artists are also working in the underground, touting fake and illegal coronavirus vaccines.
“The hidden service and anonymity afforded by the dark web have made it an ideal place for cybercriminals to sell illegal vaccines,” Trend Micro says. “A recent report talks about an underground site where operators claim to have developed a vaccine that is not only ready for purchase but also available for shipping worldwide. Another darknet site required buyers to send their personal details and even their COVID-19 infection status and known diseases to an email address. These details must also be submitted with payment in the form of Bitcoin. We believe this is a scam site.”
Interpol issued an alert in 2020 warning of organized criminal gangs advertising, selling, and administering fake vaccines.
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0





































