Palo Alto Networks and Microsoft are proud to announce the latest integration between Prisma Access and Prisma Cloud, and Microsoft Azure Active Directory (Azure AD). In this latest development, the Prisma family of products now integrates with Azure AD conditional access and directory sync functions, providing customers of these products a comprehensive joint solution for securing remote users across hybrid on-premises and multi-cloud environments. The integrations will be available for customers in October 2020.
The Challenges of Securing a Remote Workforce
The global workforce has changed significantly over the past year, and the demand for identity- and policy-driven secure access for the remote workforce has never been higher. Digital transformation and growing cloud adoption have pushed applications and services away from campus networks. The demand for greater workforce flexibility and remote work has only accelerated with the COVID-19 pandemic. Just as the home has become the new office, the resources remote workers access are everywhere – on-campus data centers as well as public and private clouds managed by multiple vendors. Physical network perimeters are no longer tied to physical locations, but are globally distributed.
This new environment brings challenges. Traditional secure remote access virtual private network (VPN) architectures are no longer sufficient or effective. With distributed applications and services across hybrid cloud and on-premises environments, users can’t simply VPN into a single data center to get the resources they need. Mobile work introduces new security risks as users access data over unsecured WiFi or unmanaged, unpatched and vulnerable user-owned devices. This leaves user credentials vulnerable to compromise and applications vulnerable to data theft. Organizations often rely on multiple authentication systems and a multitude of security products, such as web application firewalls (WAF), secure web gateways (SWG) and proxies to protect each of the services and applications users access remotely. Accessing different SaaS or data center applications across multiple locations and vendors means using different authentication interfaces and different security products. While corporate data center applications sit behind on-premises firewalls, SaaS applications for HR, billing and finance are frequently unsecured or sit behind separate cloud access security brokers (CASBs) or WAFs. As each of these products have separate interfaces and separate policies to manage, this makes rolling out uniform security policies and data center compliance across the extended enterprise increasingly difficult.
Securing a remote workforce across hybrid environments requires an identity- and policy-driven approach. This requires authenticating users, provisioning granular access and continuously monitoring the resources they access after connecting to an application or service.
Prisma Access and Prisma Cloud, With Microsoft Azure Active Directory
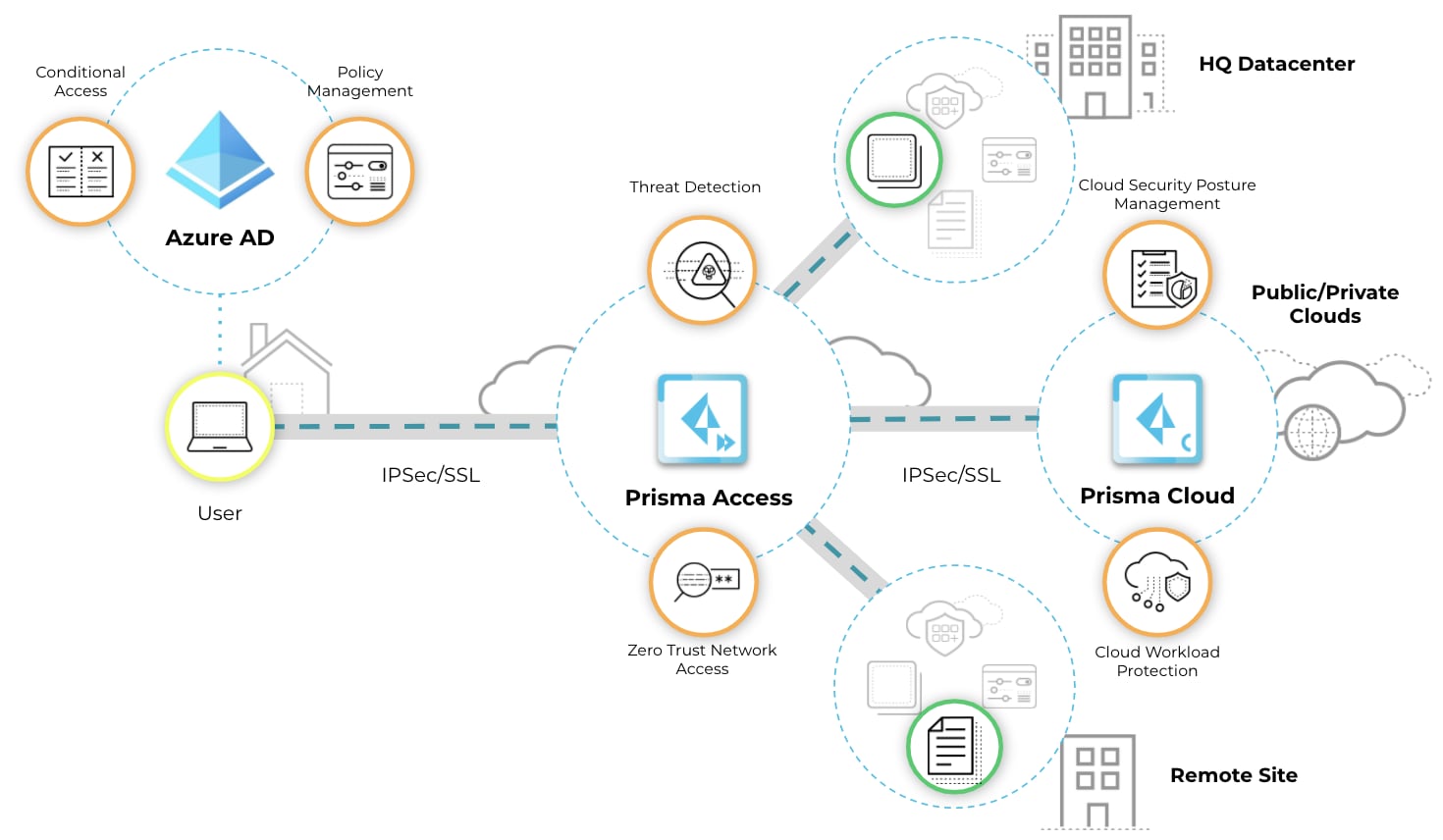
Palo Alto Networks Prisma Access and Prisma Cloud, together with Azure AD, provide a comprehensive integration to secure remote workers across hybrid-cloud infrastructure from anywhere in the world. Azure AD is a cloud-based identity and access management (IAM) solution that helps employees securely access the resources and applications they need for on-premises applications, SaaS applications and custom-built applications. Azure AD provides a single service to create and manage access control policies for all users. Through Conditional Access, Azure AD assesses customized attributes of the connecting user and their device – including device state, geographic location and user risk – to selectively provision access to applications and services.
Azure AD integrates with Prisma Access and Prisma Cloud through SAML SSO. Prisma Access is a cloud-based Secure Access Service Edge (SASE) that enables organizations to seamlessly connect and secure any user, device and application. It consolidates secure access VPN, Zero Trust Network Access (ZTNA) and Next-Generation Firewall (NGFW) capabilities into a single service edge.
Once users are authenticated through Azure AD, Prisma Access leverages information from Azure AD to provide secure, encrypted remote access to corporate resources, regardless of location. Unlike traditional legacy remote access VPN solutions, Prisma Access provides policy-controlled access to what the user needs, and only to specific applications and services. Prisma Access then performs post-connect monitoring of user traffic for signs of data loss, signatureless malware and user account compromise. With Prisma Access, mobile users no longer have to contend with multiple interfaces to access distributed applications and services, and security engineers no longer need to manage multiple security products. All corporate resources sit securely behind the global Prisma Access service edge that can be accessed anywhere, all the time.
Additionally, Prisma Cloud integrates natively with Azure AD. Prisma Cloud provides a comprehensive Cloud Native Security Platform (CNSP), combining cloud security posture management (CSPM) and cloud workload protection (CWPP) to secure your organization’s hybrid, multi-cloud infrastructure. While users are accessing their cloud-based applications, Prisma Cloud performs continuous assessment of the users and application infrastructure, integrating configuration information, audit logs and network information from Azure powered by the Microsoft Graph.
The integration between Palo Alto Networks Prisma Access, Prisma Cloud and Microsoft Azure AD provides organizations with the means to secure mobile users across hybrid environments. Integration between Azure AD conditional access and directory sync functions will be available for customers in October 2020.
Learn more about Prisma Access.
By Palo Alto Networks Source Link




















