Kaspersky researchers have deconstructed an updated, more sophisticated toolset being deployed by APT group Cycldek, which has been targeting governments in Southeast Asia since at least 2013. Among the findings was a previously unknown malware—dubbed USBCulprit—that possesses both lateral movements (ability to move through the network to obtain the targeted data) and information stealing capabilities. Not only does this malware strengthen the group’s already advanced toolkit, but it gives the actors the capability to reach air-gapped devices those that are physically isolated and not directly connected to the internet.
Cycldek (also known as Goblin Panda and Conimes) is a threat actor first discovered in 2013 that primarily focuses on high-profile targets in Southeast Asia, including large organizations and government entities. Kaspersky researchers have been closely following their most recent cyberespionage activity—dating from 2018—against government organizations across several Southeast Asian countries, namely Vietnam, Thailand, and Laos. What they’ve uncovered is a much wider toolset than expected.
Post-2018, most of the attacks have been initiated with a phishing email that contains a politically-themed RTF document. The group leverages known vulnerabilities in these documents to drop the malicious payload—malware called NewCore RAT. This malware actually consists of two variants with advanced data-stealing capabilities: BlueCore and RedCore. BlueCore appears to have been deployed against diplomatic and government targets in Vietnam, while RedCore was first deployed in Vietnam, before being found in Laos. Both download the previously unknown malware known as USBCulprit.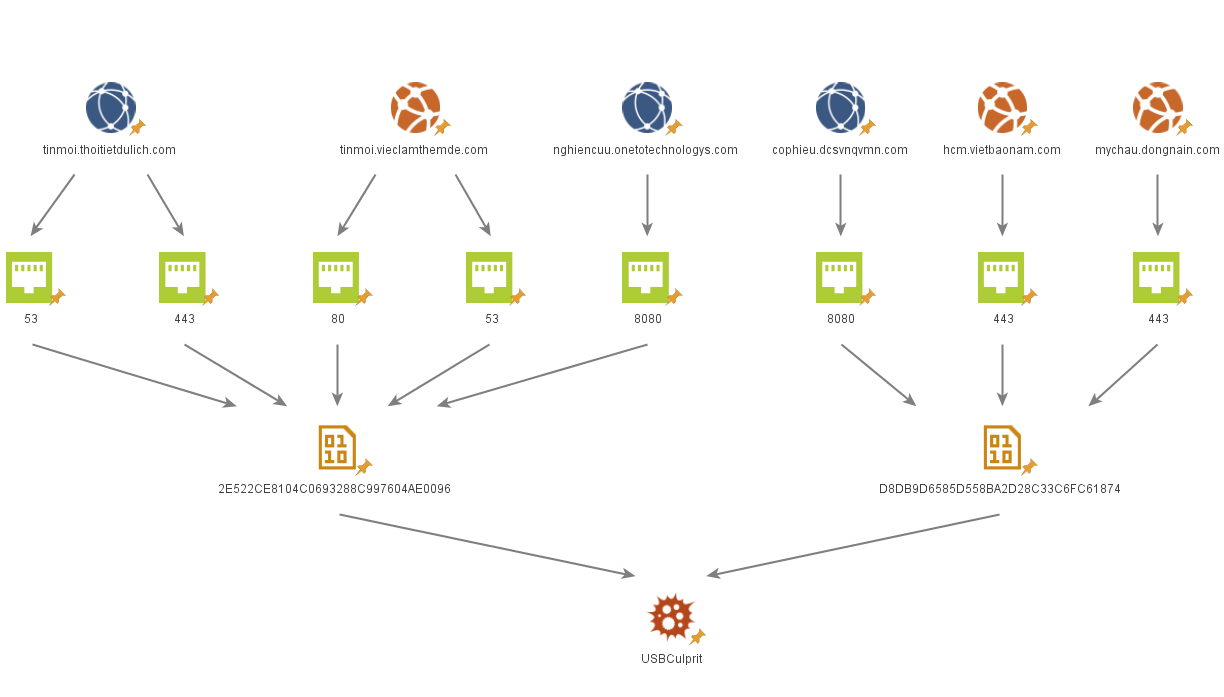
Examples of proprietary malware named USBCulprit downloaded from servers of both BlueCore and RedCoreUSBCulprit has been active since 2014, with new samples emerging as late as 2019. It possesses both lateral movement and data-stealing capabilities. Once installed, it scans various paths on the infected device, collecting documents that possess certain extensions. These documents are then transferred to USB drives connected to the system. This suggests the malware was designed to reach air-gapped machines: those that are not directly connected to the internet or any other computer connected to the internet. Often times these devices are physically isolated as well. That means the only way to transfer inbound and outbound data is with removable media—such as a USB drive.
Because the malware is not automatically launched once the infected USB is connected to a machine, it’s possible that the malware was meant to be deployed on the ground, using a human operator.
USBCulprit is capable of targeting specific files, including those last modified beyond a certain timestamp, as well as extending its capabilities. Later versions of the malware can also execute files with certain names from connected USBs. Overall, it’s a sophisticated addition to a growing list of proprietary tools used by this group. Others include a custom backdoor, a tool for stealing cookies, and a tool that steals passwords from Chromium-based browser databases.
“Our analysis has shown that this group is not the minor, less advanced actor that it was previously believed to be. In fact, it has a much wider presence in Southeast Asia—and a much more sophisticated toolset—than initial reports suggested,” comments Mark Lechtik, Senior Security Researcher at GReAT.
“It’s also likely that attacks by Cycldek against high-profile targets in Southeast Asia will continue. This group’s activity has not only not ceased since 2013, but it continues to evolve, adding new malware and targeting new countries. We will be continuing to monitor Cycldek’s activity,” adds Giampaolo Dedola, Senior Security Researcher at GReAT.
To stay safe from Cycldek and other APTs, Kaspersky experts recommend:
- Provide your Security Operations Center (SOC) team with access to the latest threat intelligence, and stay up-to-date with new and emerging tools, techniques, and tactics used by threat actors and cybercriminals.
- For endpoint level detection, investigation, and timely remediation of incidents, implement EDR solutions.
- In addition to adopting essential endpoint protection, implement a corporate-grade security solution that detects advanced threats at the network level at an early stage.
- Ensure devices, software, applications, and services are kept updated with the latest patches.
- Provide your staff with basic cybersecurity hygiene training, as many targeted attacks start with phishing or other social engineering techniques. Conduct a simulated phishing attack to ensure that they know how to distinguish phishing emails.























