A botnet used for illicit cryptocurrency mining activities is abusing Bitcoin (BTC) transactions to stay under the radar.
According to new research published by Akamai on Tuesday, the technique is being harnessed by operators of a long-running cryptocurrency mining botnet campaign, in which BTC blockchain transactions are being exploited to hide backup command-and-control (C2) server addresses.
Botnets rely on C2 servers to receive commands from cyberattackers. Law enforcement and security teams are constantly finding and taking down these C2 servers in order to render campaigns defunct — but if backups are in play, takedowns can be more difficult.
Akamai says that botnet operators are able to hide backup C2 IP addresses via the blockchain, and this is described as a “simple, yet effective, way to defeat takedown attempts.”
The attack chain begins with the exploit of remote code execution (RCE) vulnerabilities impacting software including Hadoop Yarn and Elasticsearch, such as CVE-2015-1427 and CVE-2019-9082.
In some attacks, rather than outright system hijacking, RCEs are also being modified to create Redis server scanners that find additional Redis targets for cryptocurrency mining purposes.
A shell script is deployed to trigger an RCE on a vulnerable system and Skidmap mining malware is deployed. The initial script may also kill off existing miners, modify SSH keys, or disable security features.
Cron jobs — time-based job schedulers — and rootkits are used to maintain persistence and further distribute the malware. However, in order to maintain and re-infect target systems, domains and static IP addresses are used — and these addresses are eventually identified and killed by security teams.
“Predictably these domains and IP addresses get identified, burned, and/or seized,” the researchers say. “The operators of this campaign expected this and included backup infrastructure where infections could fail over and download an updated infection that would, in turn, update the infected machine to use new domains and infrastructure.”
In December, Akamai noted a BTC wallet address was being included in new variants of the cryptomining malware. Additionally, a URL for a wallet-checking API and bash one-liners were found, and it appears that the wallet data being fetched by the API was being used to calculate an IP address.
This IP address is then used to maintain persistence. The researchers say that by fetching addresses via the wallet API, the malware’s operators are able to obfuscate and stash configuration data on the blockchain.
“By pushing a small amount of BTC into the wallet, they can recover infected systems that have been orphaned,” Akamai says. “They essentially have devised a method of distributing configuration information in a medium that is effectively unseizable and uncensorable.”
To convert wallet data into an IP address, the operators use four bash one-liner scripts to send an HTTP request to the blockchain explorer API for the given wallet, and then the Satoshi values — the smallest, pre-defined value of BTC units — of the most recent two transactions are then converted into the backup C2 IP.
“The infection is using the wallet address as a DNS like record, and the transaction values as a type of A record,” Akamai explains. “In Fig. 2 [below], the variable aa contains the Bitcoin wallet address, variable bb contains the API endpoint that returns the latest two transactions used to generate the IP address, and variable cc contains the final C2 IP address after the conversion process is completed. To achieve this conversion, four nested Bash one-liners (one each, per-octet) are concatenated together. While the mess of cURLs, seds, awks, and pipes is hard to make sense of at first glance, it’s a fairly simple technique.”
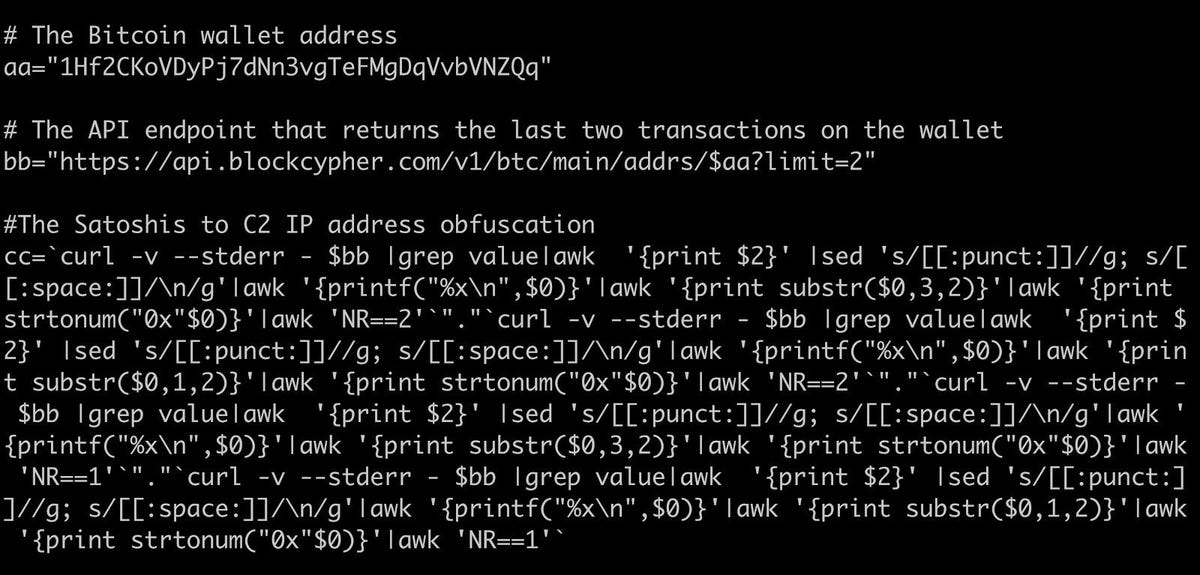
Bash script example of Satoshis to C2 IP conversion
Akamai
Akamai estimates that to date, over $30,000 in Monero (XMR) has been mined by the operators.
“The technique isn’t perfect,” the researchers noted. “There are improvements that can be made, which we’ve excluded from this write-up to avoid providing pointers and feedback to the botnet developers. Adoption of this technique could be very problematic, and it will likely gain popularity in the near future.”
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0



