It seems that Covid-19 is here to stay, at least in the foreseeable future, and for many, a vaccine is the only hope for everyone being able to return to what we once knew as normal.
This month, the top front-runners in the race to develop a Covid-19 vaccine, Oxford University, and Moderna, announced that they have had significant progress in their developments. Both organizations recently published encouraging results for their latest experiments and declared their intention to move on to the 3rd stage out of 4 in their race towards the desired vaccine.
As we’ve previously reported, threat actors and hackers have been closely following the pandemic’s development globally. The “new normal” has already brought about new cyber scams. Now, in the race for a vaccine, we’re witnessing a doubling in the number of vaccine-related new coronavirus domains between June and July. In fact, 1 out of every 25 malicious coronavirus-related websites’ landing pages is vaccine-related.
Vaccine related campaigns
Cybercriminals took advantage of the latest developments in the race to develop a vaccine, and this resulted in a malspam campaign that was seen in the wild with the email subject “URGENT INFORMATION LETTER: COVID-19 NEW APPROVED VACCINES”. These emails delivered maliciously. EXE files with the name “Download_Covid 19 New approved vaccines.23.07.2020.exe” that when clicked on, installs an InfoStealer capable of gathering information, such as login information, usernames, and passwords from the user’s computer.
Another example is an email phishing campaign that sends an email with the subject “UK coronavirus vaccine effort is progressing badly appropriate, recruiting consequence and elder adults”. The mail contains a malicious link “surgicaltoll\.com/vy2g4b\.html” which now seems to be inactive. Our further research revealed that it was used to redirect traffic to a medical phishing website; “thelifestillgoeson[.]su”, which was trying to imitate a legitimate Canadian pharmacy.
Scam logo from the website below:
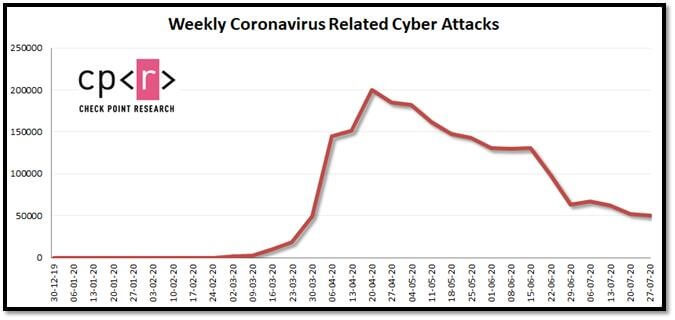
Weekly Coronavirus Related Cyber Attacks
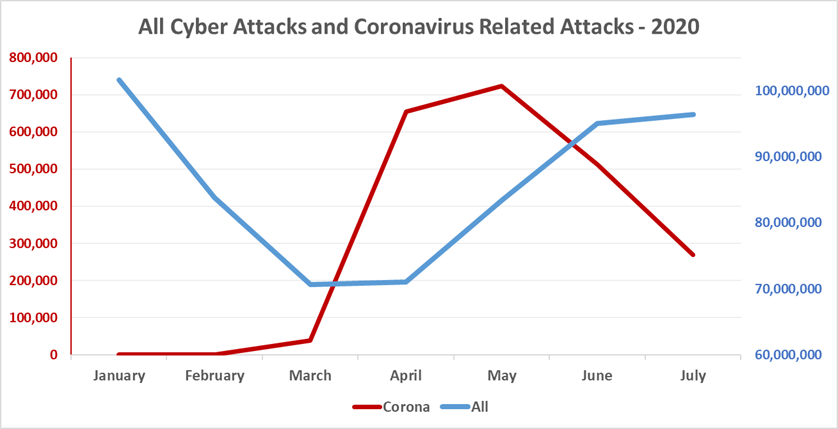
The number of general cyber-attacks remained high in July, as many countries around the globe are returning, or trying to return, to different degrees of normality. This ultimately means things are going back to (relatively) normal for hackers too.
In the meantime, the number of coronavirus-related attacks have dropped significantly. In July, we witnessed an average of about 61,000 (60, 962) corona related attacks, a decrease of over 50% when compared to the weekly average of 130,000 attacks in June.
Monthly follow up of total cyber-attacks / Coronavirus related attacks
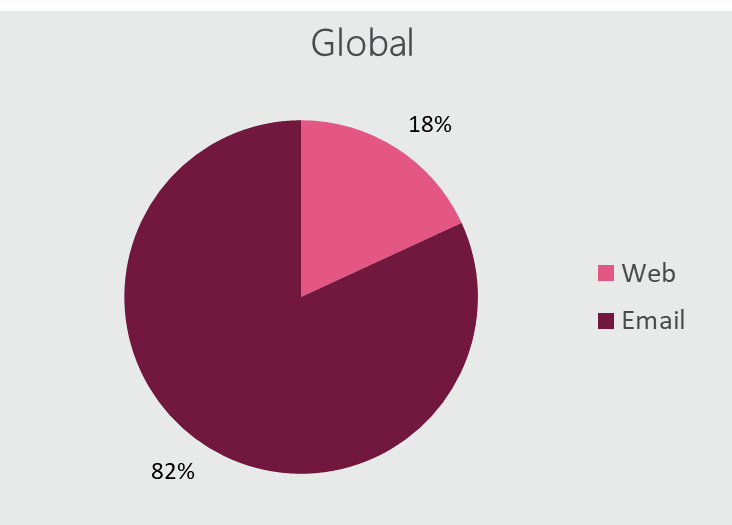
When mailboxes become your weakest link
Over 80% of attacks against organizations start from a malicious email. Since email attacks usually involve the human factor, your employees’ email inboxes are your organization’s weakest link. Closing this security gap requires protections against various threat vectors: phishing, malware, data theft and account-takeover.
This might force you to choose between the security level you need and what you can actually afford and efficiently manage. Email is the first link in a chain of attacks, and with the rise of remote working, the use of cloud mailboxes and productivity applications have been increasing exponentially.
Attack vectors for malicious files in the last 30 days
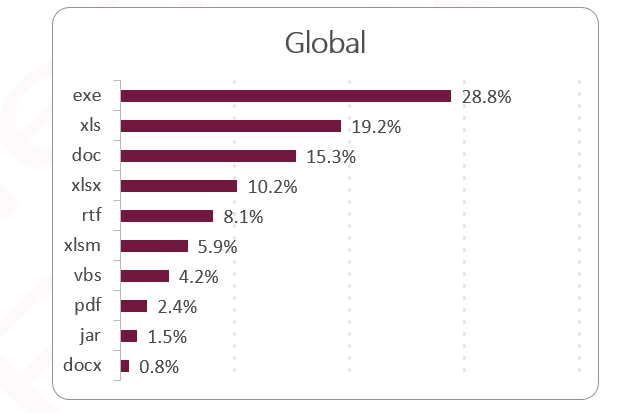
Top Malicious File Types transferred via Email- Last 30 Days
So how can you improve your organization’s resilience to email-based attacks? Here are our tips:
- Protect your email traffic with at least one layer of an advanced email security solution from a known vendor. Niche players and open-source solutions might cause more damage than good.
- Protect mobile and endpoint browsing with advanced cybersecurity solutions, which prevent browsing to phishing web sites, whether known or unknown
- Use two-factor authentication to verify any change to account information or wire instructions.
Continuously educate your end-users: whenever irreversible actions such as money transfers are conducted, details of the transaction must be verified in additional means such as voice communication and must not exclusively rely on information from email correspondence. - Check the full email address on any message and be alert to hyperlinks that may contain misspellings of the actual domain name.
- Do not supply login credentials or personal information in response to a text or email.
Regularly monitor financial accounts. - Keep all software and systems up to date.
- Make sure you are using an email security solution that blocks sophisticated phishing attacks like BEC, in order to prevent them from reaching employees mailboxes, to begin with.