What is ransomware?
Ransomware is one of the biggest security problems on the internet and one of the biggest forms of cybercrime that organisations face today. Ransomware is a form of malicious software – malware – that encrypts files and documents on anything from a single PC all the way up to an entire network, including servers. Victims can often be left with few choices; they can either regain access to their encrypted network by paying a ransom to the criminals behind the ransomware, or restore from backups or hope that there is a decryption key freely available. Or start again from scratch.
Some ransomware infections start with someone inside an organisation clicking on what looks like an innocent attachment that, when opened, downloads the malicious payload and encrypts the network.
Other, much larger ransomware campaigns use software exploits and flaws, cracked passwords and other vulnerabilities to gain access to organisations using weak points such as internet-facing servers or remote-desktop logins to gain access. The attackers will secretly hunt through the network until they control as much as possible – before encrypting all they can.
It can be a headache for companies of all sizes if vital files and documents, networks or servers are suddenly encrypted and inaccessible. Even worse, after you are attacked with file-encrypting ransomware, criminals will brazenly announce they’re holding your corporate data hostage until you pay a ransom in order to get it back.
It might sound too simple, but it’s working – to such an extent that the director of UK intelligence agency GCHQ Jeremy Fleming has warned that the threat of ransomware is “growing at an alarming rate.”
What is the history of ransomware?
While ransomware has exploded in recent years, it’s not a new phenomenon: the first instance of what we now know as ransomware appeared in 1989.
Known as AIDS or the PC Cyborg Trojan, the virus was sent to victims – mostly in the healthcare industry – on a floppy disc. The ransomware counted the number of times the PC was booted: once it hit 90, it encrypted the machine and the files on it and demanded the user ‘renew their license’ with ‘PC Cyborg Corporation ‘ by sending $189 or $378 to a post office box in Panama.
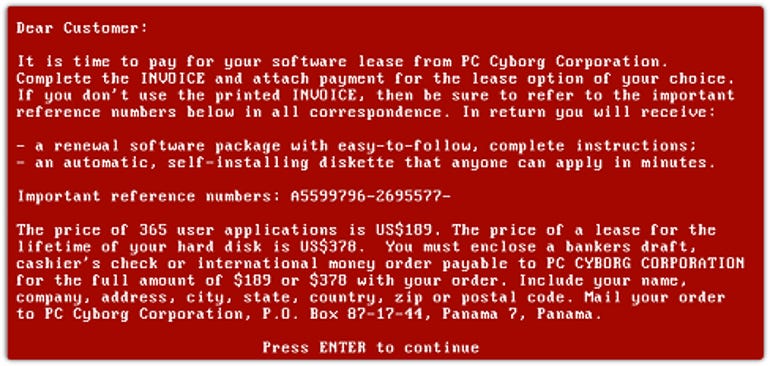
The AIDS demand for payment – by post.
Image: Sophos
How did ransomware evolve?
This early ransomware was a relatively simple construct, using basic cryptography that mostly just changed the names of files, making it relatively easy to overcome.
But it set off a new branch of computer crime, which slowly, but surely, grew in reach – and really took off in the internet age. Before they began using advanced cryptography to target corporate networks, hackers were targeting general internet users with basic ransomware.
One of the most successful variants was ‘police ransomware’, which tried to extort victims by claiming the PC had been encrypted by law enforcement. It locked the screen with a ransom note warning the user they’d committed illegal online activity, which could get them sent to jail.
However, if the victim paid a fine, the ‘police’ would let the infringement slide and restore access to the computer by handing over the decryption key. Of course, this wasn’t anything to do with law enforcement – it was criminals exploiting innocent people.
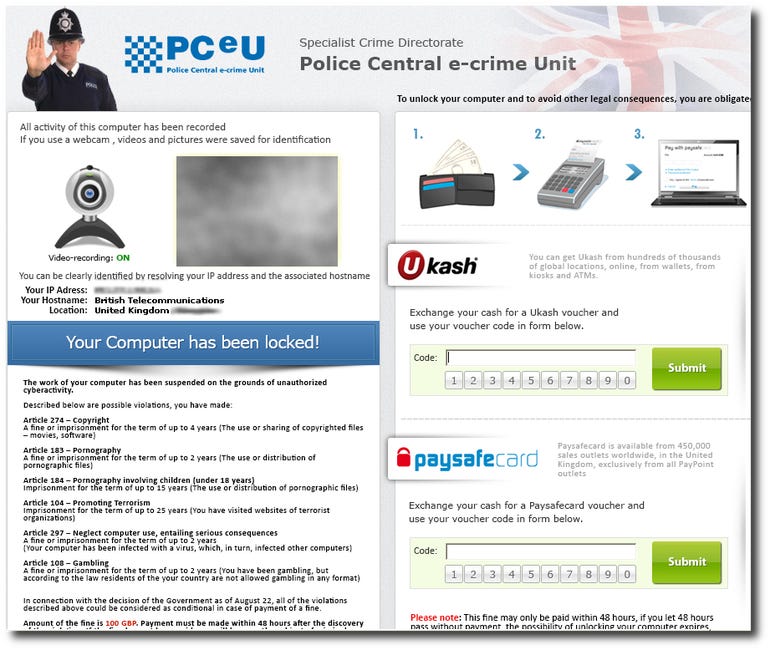
An example of ‘police ransomware’ threatening a UK user.
Image: Sophos
While somewhat successful, these forms of ransomware often simply overlaid their ‘warning’ message on the user’s display – and rebooting the machine could get rid of the problem and restore access to files that were never really encrypted.
Criminals learned from this and now the majority of ransomware schemes use advanced cryptography to truly lock down an infected PC and the files on it.
What are the main types of ransomware?
Ransomware is always evolving, with new variants continually appearing in the wild and posing new threats to businesses. However, there are certain types of ransomware that have been much more successful than others.
The most prolific family of ransomware during 2021 so far is Sodinokibi, which has plagued organisations around the world since emerging in April 2019.
Also known as REvil, this ransomware has been responsible for encrypting the networks of a large number of high-profile organisations including, Travelex and a New York law firm with celebrity clients.
The gang behind Sodinokibi spend a long time laying the groundwork for an attack, stealthily moving across the compromised network to ensure that everything possible can be encrypted before the ransomware attack is launched.
Those behind Sodinokibi have been known to demand payments of millions of dollars in exchange for decrypting the data. And given the hackers often gain full control of the network, those organisations that refuse to pay the ransom after falling victim to Sodinokibi also find the gang threatening to release stolen information if the ransom isn’t paid.
Sodinokibi isn’t the only ransomware campaign that threatens to leak data from victims as additional leverage for extorting payment; ransomware gangs like Conti, Doppelpaymer and Egregor are among those who threaten to publish stolen information if the victim doesn’t pay up.
New ransomware families are emerging all the time while others suddenly disappear or go out of fashion, with novel variations constantly emerging on underground forums. Any of the top forms of ransomware right now could be yesterday’s news in just a few months.
For example, Locky was once the most notorious form of ransomware, creating havoc within organisations around the world throughout 2016, spreading via phishing emails. Locky remained successful because those behind it regularly updated the code to avoid detection. They even updated it with new functionality, including the ability to make ransom demands in 30 languages, so criminals can more easily target victims around the world. At one point Locky became so successful, it rose to become one of the most prevalent forms of malware in its own right. However, under a year later it appeared to have disappeared and has remained unheard of since.
The following year, it was Cerber that became the most dominant form of ransomware, accounting for 90% of ransomware attacks on Windows in April 2017. One of the reasons Cerber became so popular was the way it was distributed as ‘ransomware-as-a-service’, allowing users without technical know-how to conduct attacks in exchange for some of the profits going back to the original authors.
While Cerber seemed to disappear by the end of 2017, it pioneered the ‘as-a-service’ model’ that is popular with many forms of ransomware today.
Another successful form of ransomware in 2017 and 2018 was SamSam, which became one of the first families to become notorious not just for for charging a ransom of tens of thousands of dollars for the decryption key, but exploiting unsecured internet-facing systems as a means of infection and spreading laterally across networks.
In November 2018, the US Department of Justice charged two hackers working out of Iran with creating SamSam ransomware, which is reported to have made over $6m in ransom payments over the course of a year. Shortly afterwards, SamSam appeared to cease as an active form of ransomware.
Throughout 2018 and 2019, another family of ransomware that proved problematic for both businesses and home users was GandCrab, which Europol described as “one of the most aggressive forms of ransomware” at the time.
GandCrab operated ‘as-aa-service’ and received regular updates, meaning that even when security researchers cracked it and were able to release a decryption key, a new version of the ransomware with a new method of encryption would appear soon after.
Highly successful throughout the first half of 2019 in particular, the creators of GandCrab suddenly announced the operation was shutting down, claiming to have made $2.5 million a week from leasing it out to other cyber-criminal users. GandCrab disappeared a few weeks later, although it appears as if the attackers could have just switched their focus to another campaign; researchers have suggested strong similarities in the code of GandGrab when compared to Sodinokibi, which is still going strong in 2020.
Meanwhile, one of the most successful families of ransomware during 2020 was Maze ransomware, which combined regular updates to the malware code with threats to leak stolen information if a six-figure ransom wasn’t paid. The group ‘retired’ in late 2020, but it’s suspected that a number of those behind the success of Maze have moved on to work with other criminal ransomware operations.
What was the Colonial Pipeline ransomware attack?
In May 2021, the Colonial Pipeline, which accounts for 45% of the fuel supply for the US East Coast temporarily shut down operations because of a ransomware attack.
Gasoline, diesel, jet fuel, home-heating oil, and fuel for the US military are all reliant on the Colonial Pipeline for fuel.
Fearing supply shortages due to the incident, the US Department of Transport’s Federal Motor Carrier Safety Administration (FMCSA) issued an emergency declaration, so road transport of fuel could help meet demands of those not being serviced by the pipeline shut off by ransomware.
Such was the disruption caused by the ransomware attack crippling the IT operations behind the pipeline, that President Joe Biden was briefed about it.
Some reports have said that Darkside, a ransomware-as-a-service operation, was behind the attack encrypting Colonial Pipeline’s IT network. Darkside was a relatively little known operator in the ransomware space before the Colonial Pipeline incident, but the attack demonstrated that even if the ransomware isn’t a high profile ‘brand’ on underground forums, it can still cause massive disruption.
What was WannaCry ransomware?
In what’s still regarded as the biggest ransomware attack to date, WannaCry – also known as WannaCrypt and Wcry – caused chaos across the globe in an attack that started on Friday 12 May 2017.
WannaCrypt ransomware demands $300 in bitcoin for unlocking encrypted files – a price that doubles after three days. Users are also threatened, via a ransom note on the screen, with having all their files permanently deleted if the ransom isn’t paid within a week.
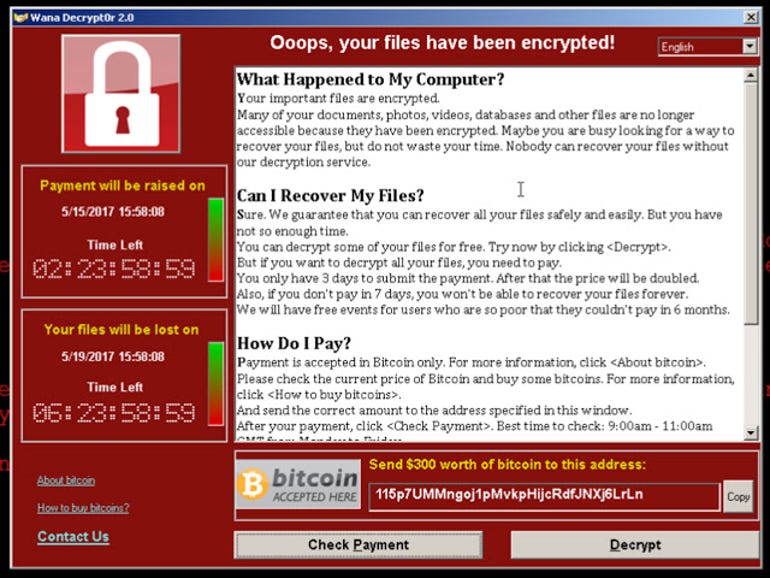
WannaCry ransomware infected Windows XP systems across the globe.
Image: Cisco Talos
More than 300,000 victims in over 150 countries fell victim to the ransomware over the course of one weekend, with businesses, governments, and individuals across the globe all affected.
Healthcare organisations across the UK had systems knocked offline by the ransomware attack, forcing patient appointments to be cancelled and led to hospitals telling people to avoid visiting Accident and Emergency departments unless it was entirely necessary.
Of all the countries affected by the attack, Russia was hit the hardest, according to security researchers, with the WannaCry malware crashing Russian banks, telephone operators, and even IT systems supporting transport infrastructure. China was also hit hard by the attack, with 29,000 organisations in total falling victim to this particularly vicious form of ransomware.
Other high-profile targets included the car manufacturer Renault, which was forced to halt production lines in several locations as the ransomware played havoc with systems.
The ransomware worm is so potent because it exploits a known software vulnerability called EternalBlue. The Windows flaw is one of many zero-days that apparently was known by the NSA – before being leaked by the Shadow Brokers hacking collective. Microsoft released a patch for the vulnerability earlier this year – but only for the most recent operating systems.
In response to the attack, Microsoft took the unprecedented step of issuing patches for unsupported operating systems to protect against the malware.
Security services in the US and the UK have since pointed to North Korea as being the perpetrator of the WannaCry ransomware attack, with the White House officially declaring Pyongyang as the source of the outbreak.
However, North Korea has labelled accusations that it was behind WannaCry as “absurd”.
No matter who was ultimately behind WannaCry, if the goal of the scheme was to make large amounts of money, it failed – only about $100,000 was paid.
It was almost three months before the WannaCry attackers finally withdrew the funds from the WannaCry bitcoin wallets – they made off with a total of $140,000 thanks to fluctuations in the value of bitcoin.
But despite critical patches being made available to protect systems from WannaCry and other attacks exploiting the SMB vulnerability, a large number of organisations seemingly chose not to apply the updates.
It’s thought that this is the reason LG suffered a WannaCry infection in August – three month after the initial outbreak. The company has since said it has applied the relevant patches.
The public dump of the EternalBlue exploit behind WannaCry has led to various hacking groups attempting to leverage it to boost their own malware. Researchers have even documented how a campaign targeting European hotels by APT28 – a Russian hacking group linked with meddling in the US presidential election – is now using the leaked NSA vulnerability.
What was NotPetya ransomware?
A little over a month after the WannaCry ransomware outbreak, the world was hit with another global ransomware attack.
This cyberattack first hit targets in Ukraine, including its central bank, main international airport, and even the Chernobyl nuclear facility, before quickly spreading around the globe, infecting organisations across Europe, Russia, the US, and Australia.
After some initial confusion as to what this malware was – some said it was Petya, some said it was something else, hence the name NotPetya – researchers at Bitdefender came to the conclusion that the outbreak was down to a modified version of Petya ransomware, combining elements of GoldenEye – a particularly vicious relative of Petya – and WannaCry ransomware into extremely potent malware.
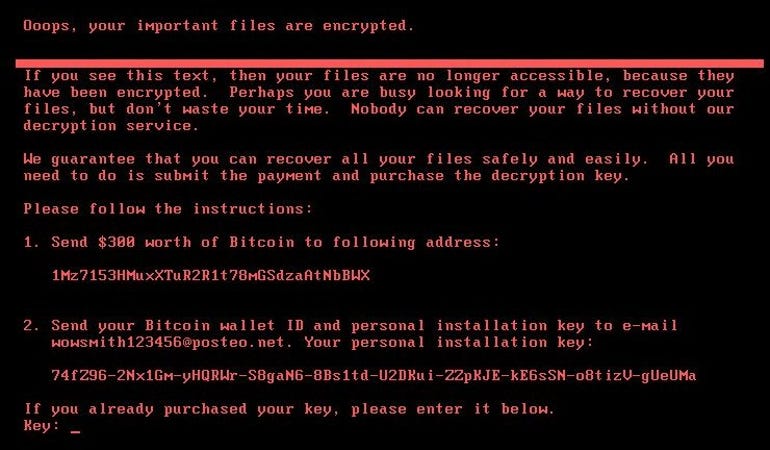
Petya ransom note.
Image: Symantec
This second form of ransomware also exploits the same EternalBlue Windows exploit that provided WannaCry with the worm-like features to spread through networks (not simply through an email attachment as is often the case) and hit 300,000 computers around the world.
However, NotPetya is a much more vicious attack. Not only does the attack encrypt victims’ files, it also encrypts entire hard drives by overwriting the master reboot record, preventing the computer from loading the operating system or doing anything.
The attackers ask for a bitcoin ransom of $300 to be sent to a specific email address, which was shut down by the email service host. However, the way this very sophisticated ransomware was apparently equipped with very basic, non-automated functions for accepting ransoms has led some to suggest that money wasn’t the goal.
This led many to believe the ransomware note was just a cover for the real goal of the virus – to cause mayhem by irrecoverably wiping data from infected machines.
Whatever the aim of the attack, it significantly impacted the finances of the organisations that became infected. UK consumer goods firm Reckitt Benckiser said it lost £100m in revenue as a result of falling victim to Petya.
But that’s a relatively modest loss in comparison to other victims of the attack: shipping and supply vessel operator Maersk and goods delivery company FedEx have both estimated losses of $300m due to the impact of Petya.
In February 2018, the governments of the United Kingdom, the United States, Australia and others officially declared that the NotPetya ransomware had been the work of the Russian military. Russia denies any involvement.
How much will a ransomware attack cost you?
Obviously, the most immediate cost associated with becoming infected with ransomware – if it’s paid – is the ransom demand, which can depend on the type of ransomware or the size of your organisation.
Ransomware attacks can vary in size but it’s becoming increasingly common for hacking gangs to demand millions of dollars in order to restore access to the network. And the reason hacking gangs are able to demand this much money is, put simply, because plenty of organisations will pay.
That’s especially the case if the network being locked with ransomware means that organisation can’t do business – they could lose large amounts of revenue for each day, perhaps even every hour, the network is unavailable. It’s estimated that the NotPetya ransomware attack cost shipping firm Maersk up to $300m in losses.
If an organisation chooses not to pay the ransom, not only will they find themselves losing revenue for a period of time that could last weeks, perhaps months, they’ll likely find themselves paying a large sum for a security company to come in and restore access to the network. In some cases, this might even cost more than the ransom demand, but at least in this instance the payment is going to a legitimate business rather than funding criminals.
Whichever way the organisation deals with a ransomware attack, it’ll also have a financial impact going forward; because to protect against falling victim again, an organisation will need to invest in its security infrastructure, even if that means ripping out the network and starting over again.
On top of all of this, there’s also the risk of customers losing trust in your business because of poor cybersecurity and taking their business elsewhere.
Why should organisations worry about ransomware?
To put it simply: ransomware could ruin your business. Being locked out of your own files by malware for even just a day will impact on your revenue. But given that ransomware takes most victims offline for at least a week, or sometimes months, the losses can be significant. Systems go offline for so long not just because ransomware locks the system, but because of all the effort required to clean up and restore the networks.
And it isn’t just the immediate financial hit of ransomware that will damage a business; consumers become wary of giving their data to organisations they believe to be insecure.
Cyber criminals have learned that it isn’t just businesses that make lucrative targets for ransomware attacks, with important infrastructure like hospitals and even industrial facilities being disrupted by ransomware – disrupting these networks can very much have consequences for people in the physical world.
Ultimately, the attackers are looking for an easy way to make money and a hospital which finds the network encrypted with ransomware can’t afford to compromise patient care by keeping the network offline for weeks to manually restore the network. That’s why, unfortunately, many ransomware victims in healthcare will pay the ransom – particularly when they were already overwhelmed by the impact of the Covid-19 pandemic.
The education sector has also become a very common target for ransomware campaigns. Schools and universities have become reliant on remote learning due to the coronavirus pandemic and cyber criminals have noticed. The networks are used by potentially thousands of people, many using their personal devices and all it might take for a malicious hacker to gain access to the network is one successful phishing email or cracking the password of one account.
The UK’s National Cyber Security Centre (NCSC) urged schools and universities to take notice of the growing threat of ransomware, after a ransomware incident led to the loss of student coursework, school financial records, as well as data relating to COVID-19 testing.
Why are small businesses targets for ransomware?
Small and medium-sized businesses are a popular target because they tend to have poorer cybersecurity than large organisations. Despite that, many SMEs falsely believe they’re too small to be targeted – but even a ‘smaller’ ransom of a few hundred dollars is still highly profitable for cyber criminals.
Why is ransomware so successful?
You could say there’s one key reason why ransomware has boomed: because it works. All it takes for ransomware to gain entry to your network is for one user to slip up and launch a malicious email attachment, or to re-use a weak password.
If organisations weren’t giving in to ransom demands, criminals would stop using ransomware. But businesses do need access to data in order to function so many are willing to pay a ransom and get it over and done with.
Meanwhile, for criminals it’s a very easy way to make money. Why spend time and effort developing complex code or generating fake credit cards from stolen bank details if ransomware can result in instant payments of hundreds or even thousands of dollars from large swathes of infected victims at once?
There are those who argue that cyber insurance is making ransomware more of a problem. Cyber insurance is a policy designed to help protect organisations from the fallout from cyberattacks.
However, some cyber insurance policies will cover paying the ransom itself – leading some cybersecurity experts to warn that cyber insurance payouts covering the cost of paying ransoms is adding to the problem, because cyber criminals know that if they hit the right target, they’ll get paid.
What does bitcoin and other cryptocurrency have to do with the rise of ransomware?
The rise of crypocurrencies like bitcoin has made it easy for cyber criminals to secretly receive payments extorted with this type of malware, without the risk of the authorities being able to identify the perpetrators.
The secure, untraceable method of making payments – victims are asked to make a payment to a bitcoin address – makes it the perfect currency for criminals who want their financial activities to remain hidden.
Cyber-criminal gangs are constantly becoming more professional – many even offer customer service and help for victims who don’t know how to acquire or send bitcoin, because what’s the point of making ransom demands if users don’t know how to pay? Some organisations have even hoarded some of the cryptocurrency in case they get infected or their files are encrypted and have to pay in bitcoin in a hurry.
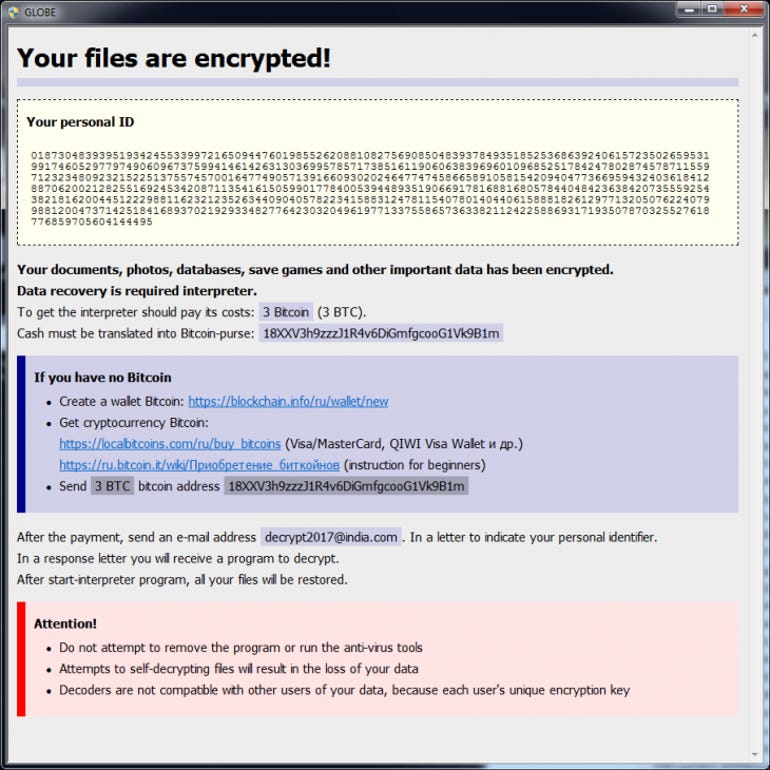
Globe3 ransom demand for 3 Bitcoin – including a ‘how to’ guide for those who don’t know how to buy it.
Image: Emsisoft Lab
How do you prevent a ransomware attack?
With large numbers of ransomware attacks starting with hackers exploiting insecure internet-facing ports and remote desktop protocols, one of the key things an organisation can do to prevent itself falling victim is by ensuring, unless it’s essential, that ports aren’t exposed to the internet if they don’t need to be.
When remote ports are necessary, organisations should make sure that the login credentials have a complex password to protect against criminals looking to deploy ransomware from being able to crack simple passwords using brute force attacks as a way in. Applying two-factor authentication to these accounts can also act as a barrier to attacks, as there will be an alert if there’s any attempt at unauthorised access.
Organisations should also make sure that the network is patched with the latest security updates, because many forms of ransomware – and other malware – are spread via the use of commonly known vulnerabilities.
EternalBlue, the vulnerability that powered WannaCry and NotPetya is still one of the most common exploits used to spread attacks – despite the security patch to protect against it having been available for over three years.
When it comes to stopping attacks via email you should provide employees with training on how to spot an incoming malware attack. Even picking up on little indicators like poor formatting, or that an email purporting to be from ‘Microsoft Security’ is sent from an obscure address that doesn’t even contain the word Microsoft within it, might save your network from infection. The same security policies that protect you from malware attacks in general will go some way towards preventing ransomware from causing chaos for your business.
There’s also something to be said for enabling employees to learn from making mistakes while within a safe environment. For example, one firm has developed an interactive video experience that allows its employees to make decisions on a series of events then find out the consequences of those at the end. This enables them to learn from their mistakes without suffering any of the actual consequences.
On a technical level, stopping employees from being able to enable macros is a big step towards ensuring that they can’t unwittingly run a ransomware file. Microsoft Office 2016, and now Microsoft Office 2013, both carry features that allow macros to be disabled. At the very least, employers should invest in antivirus software and keep it up-to date, so that it can warn users about potentially malicious files. Backing up important files and making sure those files can’t be compromised during an attack in another key.
How long does it take to recover from a ransomware attack?
Simply put, ransomware can cripple a whole organisation – an encrypted network is more or less useless and not much can be done until systems are restored.
If your organisation is sensible and has backups in place, systems can be back online in the time it takes the network to be restored to functionality, although depending on the size of the company, that could range from a few hours to days.
However, while it’s possible to regain functionality in the short term, it can be the case that organisations struggle to get all systems back up and running – as demonstrated by the Petya attack.
A month on from the outbreak, Reckitt Benckiser confirmed that some of its operations were still being disrupted and wouldn’t be fully up and running until two months on from the initial Petya outbreak.
Outside of the immediate impact ransomware can have on a network, it can result in an ongoing financial hit. Any time offline is bad for a business as it ultimately means the organisation can’t provide the service it sets out to, and can’t make money, but the longer the system is offline, the bigger that can be.
That’s if your customers want to do business with you: in some sectors, the fact you’ve fallen victim to a cyberattack could potentially drive customers away.
How do I remove ransomware?
The ‘No More Ransom‘ initiative – launched in July 2016 by Europol and the Dutch National Police in collaboration with a number of cybersecurity companies including Kaspersky Lab and McAfee – offers free decryption tools for ransomware variants to help victims retrieve their encrypted data without succumbing to the will of cyber extortionists.
The portal offers decryption tools four for families of ransomware – Shade, Rannoh, Rakhn, and CoinVault – and the scheme is regularly adding more decryption tools for even more versions of ransomware.
The portal – which also contains information and advice on avoiding falling victim to ransomware in the first place – is updated as often as possible in an effort to ensure tools are available to fight the latest forms of ransomware.
No More Ransom has grown from offering a set of four tools to carrying a vast number of decryption tools covering hundreds of families of ransomware. So far, these tools have decrypted tens of thousands of devices, depriving criminals of millions in ransoms.
The platform is now available in dozens of languages with more than 100 partners across the public and private sectors supporting the scheme.

The No More Ransom portal offers free ransomware decryption tools.
Image: Europol
Individual security companies also regularly release decryption tools to counter the ongoing evolution of ransomware – many of these will post updates about these tools on their company blogs as soon as they’ve cracked the code.
Another way of working around a ransomware infection is to ensure your organisation regularly backs up data offline. It might take some time to transfer the backup files onto a new machine, but if a computer is infected and you have backups, it’s possible just to isolate that unit then get on with your business. Just make sure that crypto-locking crooks aren’t able to encrypt your backups, too.
Should I pay a ransomware ransom?
There are those who say victims should just pay the ransom, citing it to be the quickest and easiest way to retrieve their encrypted data – and many organisations do pay even if law enforcement agencies warn against it.
But be warned: if word gets out that your organisation is an easy target for cyber criminals because it paid a ransom, you could find yourself in the crosshairs of other cyber criminals who are looking to take advantage of your weak security. And remember that you’re dealing with criminals here and their very nature means they may not keep their word: there’s no guarantee you’ll ever get the decryption key, even if they have it. Decryption isn’t even always possible: there are stories of victims making ransom payments and still not having encrypted files unlocked.
For example, a type of ransomware targeting Linux discovered earlier this year demanded a bitcoin payment but did not store encryption keys locally or through a command-and-control server, making paying the ransom futile at best.
Can you get ransomware on your smartphone?
Absolutely. Ransomware attacks against Android devices have increased massively, as cyber criminals realise that many people aren’t aware that smartphones can be attacked and the contents (often more personal than the stuff we keep on PCs) encrypted for ransom by malicious code. Various forms of Android ransomware have therefore emerged to plague mobile users.
In fact, any internet-connected device is a potential target for ransomware, which has already been seen locking smart TVs.
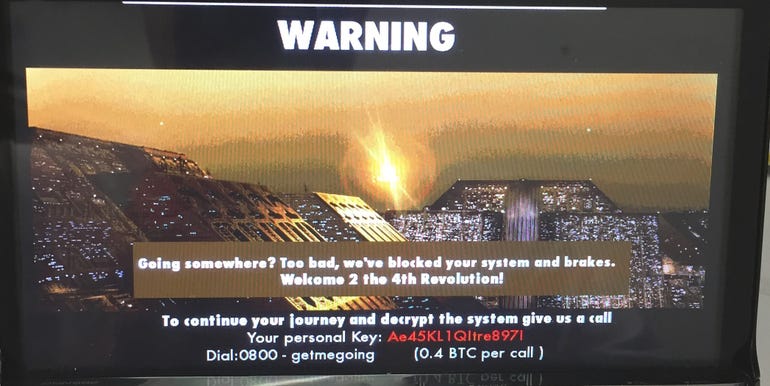
Researchers demonstrate ransomware in an in-car infotainment system.
Image: Intel Security
Ransomware and the Internet of Things
Internet of Things devices already have a poor reputation for security. As more and more of these make their way onto the market, they’re going to provide billions of new attack vectors for cyber criminals, potentially allowing hackers to hold your connected home or connected car hostage. An encrypted file is one thing: but what about finding a ransom note displayed on your smart fridge or toaster?
There’s even the potential that hackers could infect medical devices, putting lives directly at risk.
In March 2018, researchers at IOActive took this once step further by demonstrating how a commercially available robot could come under a ransomware attack. In addition to making the robot verbally demand payment in order to be returned to normal, researchers also made it issue threats and swear.
The UK’s NCSC has also warned that the growth in smart cities could also be a tempting target for cyber attackers – and it’s not hard to imagine that that holding city-wide services to a ransomware attack could be very profitable for criminals.
As ransomware continues to evolve, it’s therefore crucial for your employees to understand the threat it poses, and for organisations to do everything possible to avoid infection, because ransomware can be crippling and decryption is not always an option.



